In the previous article, we introduced some basic knowledge of digital signature and digital certificate, but we did not mention how to manage digital certificate, such as the file format of digital certificate, application and rotation of digital certificate, etc. This article will introduce the management of digital certificate.
Speaking of digital certificate management, we have to mention a proper noun: PKI (Publick Key Infrastructure), which is a key management platform following established standards and can provide cryptographic services such as encryption and digital signature and the necessary key and certificate management system for all network applications. In simple terms, it can be understood as providing cryptographic services such as encryption and digital signature and the related key and certificate management system for applications using the previously mentioned public and private key asymmetric cryptography.
PKI is neither a protocol nor a software. It is a standard, and the technologies developed under this standard to achieve the purpose of security infrastructure services are collectively called PKI.
Components of PKI
PKI, as an implementation standard, consists of a series of components:
- CA (Certificate Authority): It is the “core” of PKI, i.e. the application and issuing authority of digital certificate, CA must have authoritative characteristics, it is responsible for managing the issuance of certificates of all users (including various applications) under the PKI structure, bundling the public key of the user with other information of the user, verifying the identity of the user on the Internet, CA is also responsible for the blacklist registration and blacklist release of the user certificate.
- X.509 Directory Server: The X.500 Directory Server is used to “publish” user certificates and blacklist information so that users can query their own or others’ certificates and download blacklist information via the standard LDAP protocol.
- Secure Socket Layer (SSL) based secure web server: Originally developed by Netscape, the Secure Socket Layer (SSL) protocol has become a global standard used by the web to identify websites and web surfers, and to encrypt communications between browser users and web servers.
- Web Secure Communication Platform: Web has two parts: Web client and Web server, which guarantees the confidentiality, integrity and authentication of client-side and server-side data through SSL protocol with high-strength cryptographic algorithms.
- Self-developed Security Applications: Self-developed security applications refer to various specific applications developed by various industries, such as banking and securities applications, etc. The complete PKI includes:
- Authentication policy development
- Authentication rules
- The development of the operational system
- The content of the legal relationship between the parties involved
- Implementation of the technology, etc.
Certificate Authority
Certificate Authority, also known as CA, is an authority responsible for issuing and managing digital certificates, and as a trusted third party in e-commerce transactions, it assumes the responsibility of verifying the legitimacy of public keys in the public key system. CA issues a digital certificate for each user who uses the public key to realize the distribution of the public key and prove its legitimacy. As the core part of PKI, CA implements some important functions in PKI:
- receiving applications to verify end-user digital certificates
- determining whether to accept the application for end-user digital certificate - approval of certificate
- issuing and refusing to issue digital certificate to the applicant - certificate issuance
- receiving and processing the end-user’s digital certificate renewal request - certificate renewal
- receiving end-user digital certificate inquiry and revocation
- generating and issuing certificate revocation list
- archiving of digital certificates.
- key archiving.
- archiving of historical data.
X.509 Certificate Standard
There are many format standards in the whole PKI system, and the standards of PKI stipulate the design, implementation and operation of PKI and the “rules of the game” for various roles of PKI. If two PKI applications want to interact with each other, the interaction can only be carried out properly if they understand each other’s data meaning, and the role of standards is to provide a common agreement on data syntax and semantics. The most important standard in PKI, it defines the basic structure of public key certificates.
X.509 is the basic standard that defines the structure of public key certificates, and is a very common certificate format at present.
X.509 plays a pivotal role in PKI, which has grown from small to large, from a closed network environment to a distributed open environment. It can be said that the X.509 standard is the prototype of PKI.
RFC5280 specifies the standard format of x.509 certificate as shown in the following figure.
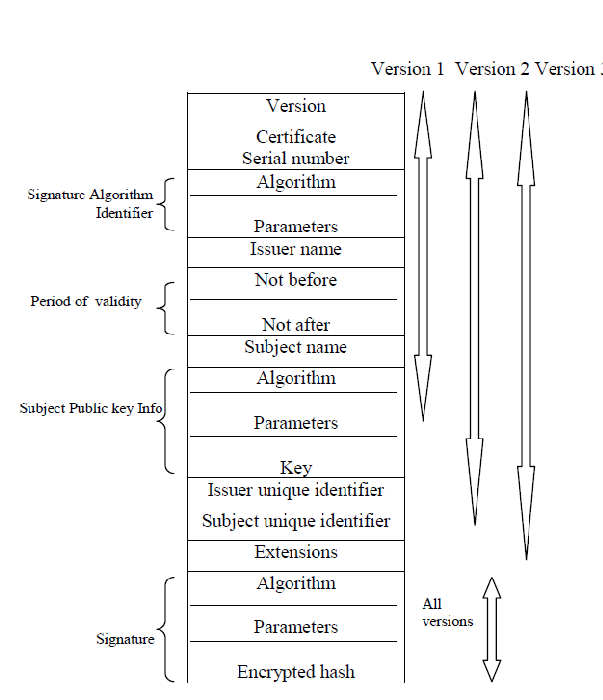
For X.509-compliant digital certificates, it must be ensured that the public key and the name of its owner (Subject) are the same, and that the certificate issuer (Issuer) is always a CA or a person designated by a CA. An X.509 digital certificate is a collection of standard fields that contain information about the user or device and its corresponding public key. The X.509 standard defines what information should be contained in the certificate and describes how such information is encoded (i.e. data format). All X.509 certificates contain the certificate issuer’s information in addition to the certificate owner’s public key, some basic information of the certificate owner and digital signature. Specifically, it contains the following data.
- Version: indicates which version of X.509 standard (Version 1, Version 2 or Version 3) is used in the certificate, the version number affects some specific information in the certificate, the latest version is
Version: 3. - Serial Number: a unique integer that identifies the certificate and is assigned by the certificate issuer as the unique identifier of this certificate.
- Signature Algorithm Identifier: the algorithm identifier used for the visa certificate, consisting of an object identifier plus relevant parameters to indicate the digital signature algorithm used for this certificate. For example, the
sha256WithRSAEncryptionobject identifier is used to indicate that the digital signature is a hash encryption of sha256 using RSA. - Validity period (Validity): the certificate start date and time and termination date and time; specify that the certificate is valid within these two times.
- Subject Information: the unique identifier (or DN) of the certificate holder which name should be unique on the Internet.
- Public Key Information (Subject Public Key Info): including the certificate holder’s public key, algorithm (specifying which cryptosystem the key belongs to) identifier and other relevant key parameters.
- Issuer Unique Identifier (Issuer): identifier - unique identifier of the certificate issuer, required only in versions 2 and 3, and is optional.
- Certification Authority Digital Signature: this is a signature generated using the certificate issuer’s private key to ensure that this certificate has not been altered after it has been issued.
- Certification Authority: The identifiable name (DN, Distinguished Name) of the certificate issuer, which is the X.509 name of the unique CA of the entity issuing this certificate. Use of this certificate implies trust in the entity that issued the certificate. (Note: In some cases, such as root or top-level CA certificates, the issuer issues the certificate itself).
In addition to the above fields, X.509 certificates can include optional standard and specialized extensions (only available in versions 2 and 3), which are not described here.
Here is the information about my personal certificate created using openssl.
|
|
Digital Certificate Formats
A digital certificate is embodied as an associated encrypted data file or a series of associated encrypted data files, commonly used in the following formats.
- Conforms to the
PKI ITU-T X509standard, legacy standard (.DER .PEM .CER .CRT) - Compliant with the
PKCS#7encrypted message syntax standard (.P7B .P7C .SPC .P7R) - Compliant with
PKCS#10Certificate Request Standard (.p10) - Conforms to
PKCS#12Personal Information Exchange Standard (.pfx *.p12)
Of course, these are only a few of the commonly used standards, of which there are two other encoding forms for X509 certificates.
X.509 DER(Distinguished Encoding Rules) encoding with the suffix:.DER .CER .CRTX.509 BASE64encoding, suffix is:.PEM .CER .CRT
X.509 is the basic standard for digital certificates, while P7 and P12 are the two implementation specifications, P7 for digital envelopes and P12 for certificates with private keys. The contents of the generated digital certificate may be different depending on the adopted standard. The following is a summary of what the certificate contains/may contain, and the general certificate features are as follows
- Storage format: binary or ASCII
- whether to include the public key, private key
- contains a certificate or multiple certificates
- whether to support password protection (for the current certificate)
Among them.
DER, CER, CRTholds the certificate in binary form, with only the public key and no private key.CSRcertificate request.PEMstores the certificate in Base64 encoded form, encapsulated with--BEGIN CERTIFICATE--and--END CERTIFICATE--encapsulation, public key only.-PFXand-P12also store certificates in binary form, containing public and private keys and including protection passwords. The storage formats ofPFXandP12are exactly the same, only the extensions are different.P10certificate request.P7Ris CA’s reply to certificate request, generally doing digital envelope.P7B/P7Ccertificate chain, which can contain one or more certificates.
For example, PFX and P12 also store the certificate in binary form; DER indicates the certificate and has signature, in actual use, there is DER encoded private key without signature, which is actually just a “middleware”; in addition, the certificate signature request generally uses CSR extension, but its format may be PEM or DER format, but they all represent the certificate request, and the real certificate can be obtained only after CA issuance.