In the process of using Linux, many people like me often come across iptables, but they only know it as a tool to set up Linux firewall, but they don’t know how it works. Today, we will start from scratch to understand how iptables works on Linux.
iptables is a part of the netfilter project, a common firewall software on Linux, so to talk about iptables, let’s first sort out what a firewall is.
What is a firewall
Simply put, a firewall is a network isolation tool deployed at the edge of a host or network, with the goal of matching network messages to and from the host or local network according to predefined rules, and doing the defined processing (allow, deny, forward, discard, etc.) for the corresponding network messages if the rules match successfully. Firewalls can be divided into host firewalls and network firewalls according to the scope of their management; they can be divided into packet filtering firewalls (netfilter) and proxy servers (Proxy) according to their working mechanism. In this note, we will focus on packet filtering firewalls (netfilter).
Note: Some people also classify TCP Wrappers as a type of firewall, which is a tool that handles network packets based on the name of the service program software.
Packet Filtering Firewall
The packet filtering firewall relies on the Linux kernel software netfilter, a Linux kernel “security framework”, and iptables, a configuration tool for the kernel software netfilter, which works in user space. iptables/netfilter combination The iptables/netfilter combination is a filtering firewall for the Linux platform, and is a free alternative to commercial firewall software for filtering, modifying, redirecting, and converting (nat) network packets.
Note: On some Linux distributions, we can use
systemctl start iptablesto start the iptables service, but it should be noted that iptables is not and does not depend on a daemon, it just takes advantage of the functionality provided by the Linux kernel.
Linux network administrators configure iptables rules and the corresponding network packet processing logic to perform the corresponding pre-defined processing logic when the network packet matches such rules. This can be briefly summarized as follows.
where the rules can include the source address, destination address, transport layer protocol (TCP/UDP/ICMP/…) of the matching data message and application layer protocols (HTTP/FTP/SMTP/…) etc. The processing logic is to handle these packets according to the methods defined by the rules, such as accept, reject, drop, etc.
The netfilter is a series of hooks in the kernel space that register callback functions for kernel modules at different locations in the network stack. In other words, it does the corresponding processing logic configured by iptables when packets pass through different locations on the network stack. The five hooks in netfilter (also referred to here as the five gates) are PRE_ROUTING/INPUT/FORWARD/OUTPUT/POST_ROUTING, and the flow diagram of network packets is shown in the following figure.
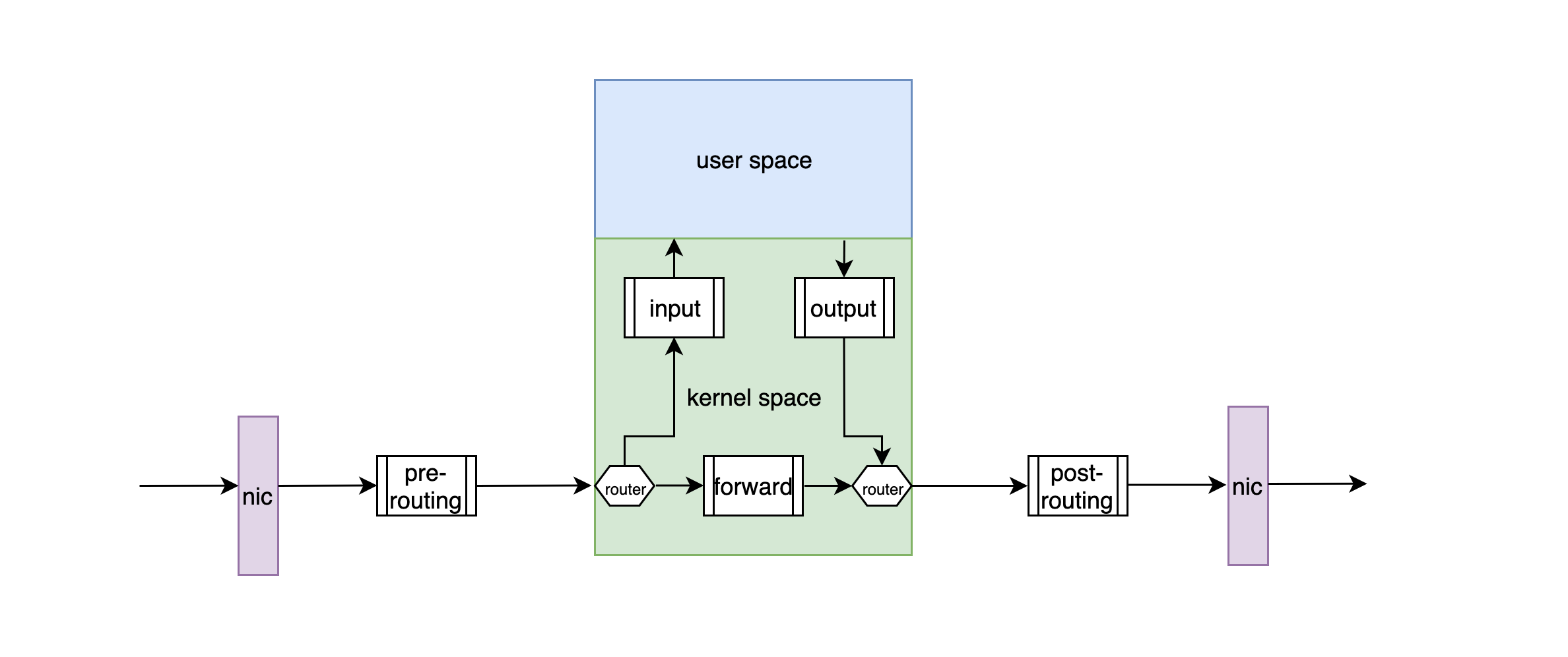
- When a packet is received by the host/network server NIC, it enters the network stack in kernel space for layer-by-layer decapsulation.
- When a packet just entering the network layer passes through the PRE_ROUTING barrier, a routing process is performed. When the destination address is the local address, the data enters INPUT and the non-local destination address enters FORWARD (requires local kernel support for IP_FORWARD), so the destination address translation is usually performed at this barrier.
- INPUT packets sent to local after routing pass through this barrier, so filtering INPUT packets is done at this point in the barrier
- FORWARD Packets to be forwarded after routing pass through this gate, so network firewalls are usually configured at this gate
- OUTPUT The packets generated by the local user space application process pass through this barrier, so OUTPUT packet filtering is performed at this barrier
- POST_ROUTING The packets just passed through the FORWARD and OUTPUT barriers are routed once to choose which interface to send to the network. After routing, packets pass through the POST_ROUTING barrier, and source address translation is usually performed at this point
The above-mentioned “gateways” in the network stack are called “chains” in iptables terminology, and the built-in chains include the five mentioned above.
- PreRouting
- Forward
- Input
- Output
- PostRouting
In a general scenario, the flow of packets is basically as follows.
- Packets to a process on this host: PreRouting -> Input -> Process -> Output -> PostRouting
- Packets forwarded by this host: PreRouting -> Forward -> PostRouting
The four tables and five chains of iptables
iptables has five chains by default, corresponding to the five levels mentioned above: PRE_ROUTING/INPUT/FORWARD/OUTPUT/POST_ROUTING, which are triggered by netfilter’s five hook functions. But why is it called a “chain”? As we know, the iptables/netfilter firewall matches the “rules” of the packets passing through and then performs the appropriate “processing”. When a message passes through a certain barrier, there is more than one “rule” on this barrier, and many rules will be matched one by one in order, so it is appropriate to organize all the rules at this barrier as a “chain”. For the network packets passing through the corresponding barrier, the “rules” are matched one by one in order.
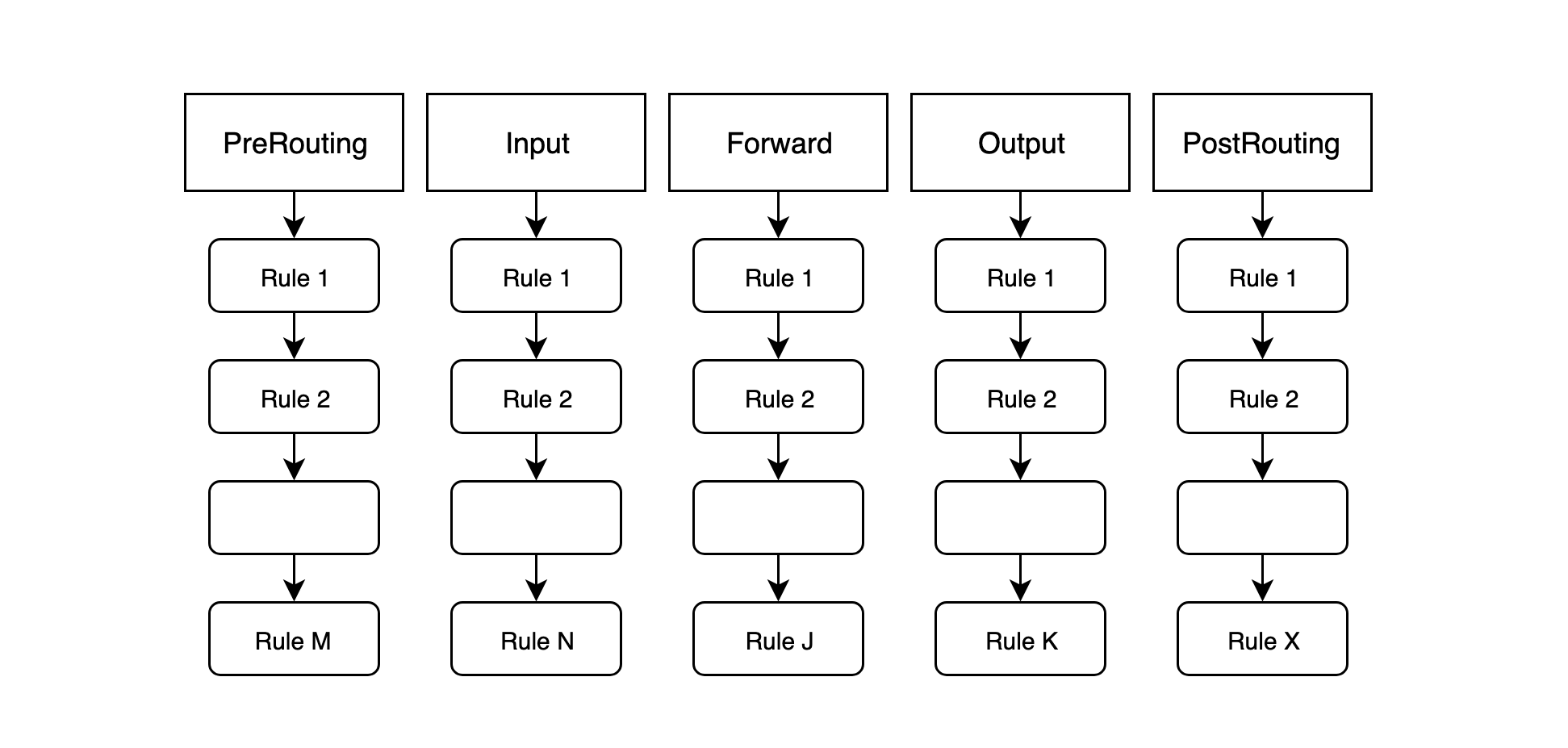
Another problem is that some of the rules in each “chain” have similar functions, for example, class A rules are all about filtering IPs or ports, and class B rules are all about modifying messages, so we consider whether we can put these rules with similar functions together so that it will be easier to manage iptables rules. iptables calls a collection of rules with the same function a “table”, and defines four types of tables.
- filter table: responsible for filtering function; the corresponding kernel module is iptables_filter
- nat (Network Address Translation) table: network address translation functions, such as SNAT, DNAT, the corresponding kernel module is iptables_nat
- mangle table: unpacking messages, modifying and sealing packets, the corresponding kernel module is iptables_mangle
- raw table: disables the connection tracking mechanism enabled on the nat table; the corresponding kernel module is iptables_raw
All the iptables “rules” defined by the Linux network administrator are present in these four tables.
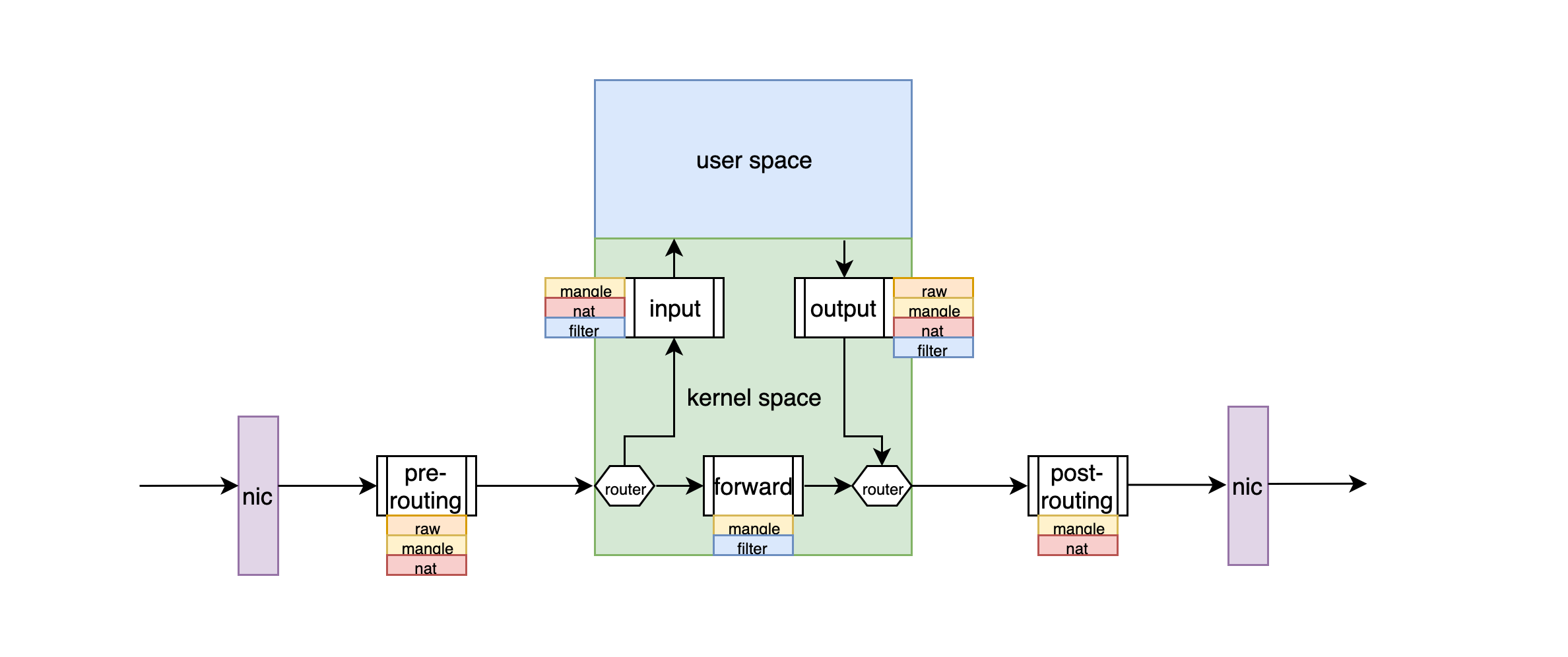
However, it is important to note that not all “chains” have all types of “rules”, that is, “rules” in a particular table are not meant to be applied to some “chains”. “For example, the “rules” in the nat table used for address translation cannot exist in the FORWARD “chain”. Below, we will list the “chain, table” relationship of iptables in detail.
Let’s start with the rules of what functions each “chain” has.
| chain | table |
|---|---|
| PreRouting | raw, mangle, nat |
| Forward | mangle, filter |
| Input | mangle, filter, nat |
| Output | raw, mangle, filter, nat |
| PostRouting | mangle, nat |
When using iptables to configure rules, we often use “table” as the entry point to make “rules”, so we transform the “chain table” relationship into a “table chain” relationship.
| table | chain |
|---|---|
| raw | PreRouting, Output |
| mangle | PreRouting, Forward, Input, Output, PostRouting |
| filter | Forward, Input, Output |
| nat | PreRouting, Input, Output, PostRouting |
Another point to note is that, as the packets pass through a level, all the “rules” in the “chain” are matched in order, one by one, for “rules” with the same function belong to the same “table”. So, which rules in the “table” will be placed at the top of the “chain”? This is where the question of priority comes into play. iptables provides us with four “tables”, and when they are in the same “chain”, their execution priority is as follows.
|
|
In fact, network administrators can also use iptables to create custom “chains” where rules set for a particular application layer are placed in the custom “chain”. However, custom “chains” cannot be used directly, and can only be invoked by a default “chain” as a processing action. You can say this. Custom chains are “short” chains, and these “short” chains cannot be used directly, but need to be “referenced” by the built-in chains on iptables.
The flow of packets through a filtering firewall
With the previous introduction we can summarize the flow of packets through the filtering firewall as shown in the figure below.
iptables rules
As we mentioned earlier, iptables rules consist of two parts: the matching conditions of the message and the processing actions after the match.
- Matching conditions: Matching conditions are specified based on protocol message characteristics, basic matching conditions and extended matching conditions
- processing actions: built-in processing mechanism by iptables itself to provide some processing actions
Also, network administrators can use iptables to create custom chains that are attached to the five built-in chains of iptables.
Note: Messages do not pass through the custom chain, but can only be referenced in the built-in chain after the rule takes effect, which means that the custom chain is a collection of processing actions for the rule.
Here are some points to consider when setting up iptables rules.
-
Which “table” to add to, depending on the function to be performed.
-
Which “chain” to add to based on the path the message is flowing through.
- Messages to a process on this host: PreRouting -> Input -> Process -> Output -> PostRouting
- Messages forwarded by this host: PreRouting -> Forward -> PostRouting
For each “chain” of its “rules” matching order, a good check order can effectively improve performance, so certain rules are implied.
- Rules of the same class (access to the same application), match the smallest range on top.
- Rules of different classes (accessing different applications), those that match to messages more frequently are put on top.
- Combine multiple rules that can be described by a single rule into one.
- Set the default policy.
Also, be sure to pay attention to the following when configuring the firewall for remotely connected hosts.
- Do not change the default policy of “chain” to deny, because there is a possibility of configuration failure or clear all policies can not log in to the server, but try to use rule entries to configure the default policy.
- To prevent yourself from being denied by the wrong policy, you can set a scheduled task to clear the policy when you configure the policy, and close the scheduled task when you are sure there is no error.
Configuration syntax of iptables
The configuration syntax of iptables is structured as follows.
|
|
Options
|
|
parameters
| parameter | Function |
|---|---|
| -P | Set default policy:iptables -P INPUT (DROP) |
| -F | Clear Rule Chain |
| -L | View Rule Chains |
| -A | Add a new rule at the end of the rule chain |
| -I | num Add a new rule to the head of the rule chain |
| -D | num Delete a rule |
| -s | Match source address IP/MASK with exclamation mark “!” to indicate other than this IP. |
| -d | Matching target address |
| -i | NIC Name Matches the data flowing from this NIC |
| -o | NIC Name Match the data flowing from this NIC |
| -p | Matching protocols, such as tcp, udp, icmp |
| -dport num | Matching target port number |
| -sport num | Matching source port number |
Command options input order
|
|
For details on the iptables command, please refer to https://wangchujiang.com/linux-command/c/iptables.html