What is a DNS server?
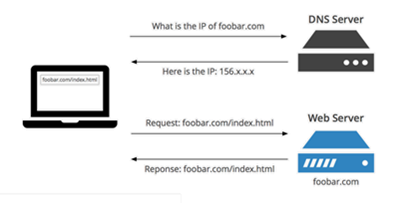
DNS, or Domain Name System, is a basic service in computer networks. Generally speaking, there are two ways to access a host on the network: by host name, or by IP address. In the Internet, using an IP address to communicate with a server simply does not work for the following reasons.
- IP addresses are not easy to remember
- IP addresses change frequently, so accessing a machine by IP address can be problematic
DNS it provides a service that is used to convert domain names to IP addresses or to convert IP addresses to domain names. DNS it works as a distributed database that maps domain names and IP addresses to each other, enabling easier access to the Internet. It is an application layer protocol DNS uses TCP and UDP port 53.
Domain Name
ICANN
The top governing body for domain names worldwide is an organization called ICANN (Internet Corporation for Assigned Names and Numbers). It is based in California, USA. It was originally a non-profit organization under the U.S. Department of Commerce, so there is some truth to the claim that the U.S. government controls domain names around the world. in 2016, the U.S. government announced that ICANN was no longer affiliated with the Department of Commerce and had become a self-managed, independent organization. But as you can imagine, the U.S. government still has absolute influence over it.ICANN is responsible for managing the operation of the worldwide domain name system. One of its main tasks is to define the top level domain (TLD for short).
TLD
The so-called top-level domain (TLD) is the highest level domain name. Simply put, it is the last part of the URL. For example, the top-level domain name for the URL www.example.com is .com.
ICANN is then responsible for specifying which strings can be used as top-level domains. As of July 2015, there are 1,058 top-level domains. They can be divided into two categories.
- One category is general top-level domains (gTLDs), such as
.com,.net,.edu,.org,.xxx, etc. There are more than 700 of them. - One category is country-specific top-level domains (ccTLDs), representing different countries and regions, such as
.cn(China),.io(British Indian Ocean Territory),.cc(Cocos Islands),.tv(Tuvalu), etc. There are more than 300 of them.
TLD hosting provider
ICANN itself will not manage these TLDs because it simply can’t. Think about it, there are over 1000 top-level domains, and there are many wholesalers under each top-level domain, and it would be too much trouble to manage each one.
ICANN’s policy is that each TLD gets a hosting provider and all matters for that domain are handled by the hosting provider, ICANN only contacts the hosting provider, which makes it much easier to manage. For example, the hosting provider for .cn domain names is the China Internet Network Information Center (CNNIC), which determines various policies for .cn domain names.
Currently, the world’s largest TLD hosting provider is Verisign, a commercial company headquartered in Virginia, USA. It hosts four general TLDs, .com, .net, .name, .gov, and two country TLDs, .cc and .tv. In addition, the back-end administration of .edu and .jobs is outsourced to it. Its exclusive monopoly on .com and .net is a historical one. In the early days, Network Solutions was commissioned by the National Science Foundation to manage the top-level domains, and in 2000, Verisign acquired the company and inherited the domain name business. 2003, Verisign sold its domain name registration business and kept only the top-level domain management. In 2010, Verisign sold its website security and encryption certificate business to Symantec Corporation. The latter in turn sold this business to DigiCert in 2017.
Verisign is ICANN’s largest hosting provider, so the two companies should have a good relationship. The truth is that they have a very poor relationship and have even been involved in lawsuits. The reason is that ICANN is a government-backed non-profit organization that does not aim to make a profit, while Verisign is a commercial company that seeks to maximize profits and must pay a large amount of hosting fees to the former every year. This is where the conflict between the two companies stems from.
In 2003, Verisign launched a new business, Site Finder, where users visiting unregistered .com or .net domains were directed to Verisign’s Web site. This meant that it owned, in effect, all unregistered .com and .net domains. Within days, Verisign had squeezed into the top 10 websites in the world, and ICANN demanded that Verisign stop the business immediately, or it would terminate the domain hosting contract.
Verisign relented and stopped the business, but then took ICANN to court, asking the court to clarify the contract between the two and whether ICANN had the authority to interfere with its business. ICANN agreed to extend Verisign’s TLD hosting contract, and agreed to increase the maximum fee Verisign charges consumers for a single domain name registration from $6 to $7.85. This fee rate, which continues to be used today, is the $0.18 you pay to register a .com or .net domain name, which is the administrative fee charged by ICANN, $7.85 is the hosting fee charged by Verisign, and the rest of the money is the domain name retailer’s fee.

If a .com or .net domain sells for $10, ICANN and Verisign take a combined $8.03. Verisign’s TLD hosting contract has since been extended twice, with the current contract not due to expire until 2024.
On the face of it, ICANN has given Verisign a huge monopoly profit. (A company once offered to lower the hosting fee for a single domain name to $1 per year if it was allowed to host the .com domain.) But in reality, ICANN is exerting market power in another way: it keeps increasing the number and variety of top-level domains. If you think a .com domain is too expensive, you can apply for other TLDs, and there are more than 1,000 TLDs to choose from.
root domain
Since ICANN manages all top-level domains, it is the highest level domain name node and is called the root domain (root domain). In some cases, www.example.com is written as www.example.com., i.e. there is an extra dot at the end. This point is the root domain name.
Theoretically, all domain name queries must first look up the root domain, because only the root domain can tell you which server manages a particular TLD. In fact, this is true, as ICANN maintains a list of top-level domains and their corresponding hosting providers. For example, if I want to go to www.example.com, I have to ask ICANN’s root domain list, which tells me that the .com domain is hosted by Verisign, and I have to go to Verisign, which tells me where the example.com server is. Then, for example, if I want to access abc.xyz, I have to go to the root list and it will tell me that the .xyz domain is hosted by CentralNic. The root list also states that .google is hosted by Google, .apple is hosted by Apple, and so on. Since the root domain list rarely changes and most DNS providers provide a cache of it, queries for root domains are actually not that frequent.
DNS root zone
The official name of the root domain list is the DNS root zone (DNS root zone), and this root zone file can be viewed on the ICANN official website. This file holds hosting information for all top-level domains, so it is very large, over 2MB. for example, 13 name servers can be found for the top-level domain .com.
|
|
In other words, the resolution result of .com domain name can be queried to any one of these 13 servers. Careful readers may notice that these servers themselves are also identified using domain names (e.g. a.gtld-servers.net.), so one would also have to query the servers they point to, which could easily result in circular queries. Therefore, the DNS root zone will also provide the IP addresses (IPv4 and IPv6) of these servers as well.
|
|
root name server
The server that holds the DNS root zone file is called the DNS root name server (root name server). Since early DNS queries resulted in a 512-byte UDP packet. This packet could hold the addresses of up to 13 servers, so it was specified that there were 13 root name servers worldwide, numbered from a.root-servers.net all the way up to m.root-servers.net. 1 is the primary root server in the United States, operated by Network Solutions, an American Internet agency. The remaining 12 are all secondary root servers, 9 of which are in the United States, 2 in Europe (located in the United Kingdom and Sweden), and 1 in Asia (located in Japan). You can find information on all root name servers at http://root-servers.org.
On the basis of full compatibility with the existing IPv4 root server architecture, Project Snowman completed the installation of 25 IPv6 root servers in 16 countries worldwide in 2016, in fact forming a new pattern of 13 original roots plus 25 IPv6 roots. A solid foundation has been laid for the establishment of a multilateral, democratic and transparent international Internet governance system. China has deployed four of them, consisting of one primary root server and three secondary root servers, breaking the dilemma of no root server in China in the past.
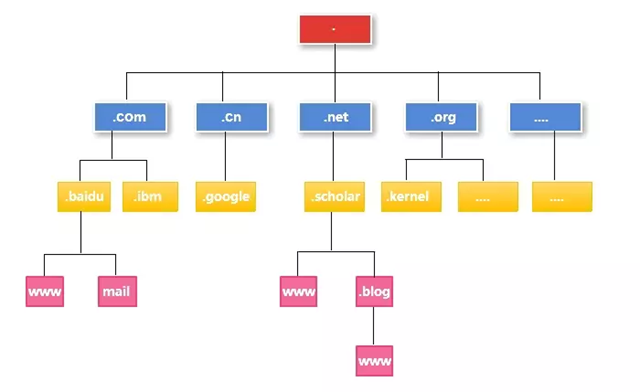
Domain
DNS is a distributed database, the naming system uses a hierarchical logical structure like an inverted tree, this logical tree structure is called a domain name space, as DNS divides the domain name space, so each organization can use their own domain name space to create DNS information.
Each node of the DNS tree represents a domain. The entire domain name space is divided by these nodes into a hierarchy. The name of each domain in the domain name space is represented by a domain name. It is usually identified by a Fully Qualified Domain Name (FQDN) that accurately represents its location relative to the root of the DNS domain tree, which is the complete representation of the node to the root of the DNS tree. From the node to the root of the tree is written in reverse and each node is separated by a “.” For the DNS domain biaodianfu, its fully qualified domain name (FQDN) is biaodianfu.com. For example, biaodianfu is a subdomain of com domain, which is represented as biaodianfu.com, while www is a subdomain of google domain, which can be represented by www.biaodianfu.com.
Usually FQDN has strict naming restrictions, the length cannot exceed 256 bytes, only characters a-z, 0-9, A-Z and minus sign (-) are allowed. Dot (.) is only allowed between domain name symbols (e.g. “biaodianfu.com”) or at the end of FQDN. Domain names are not size specific and can be divided from the top level to the bottom level: root, top level, second level, and subdomain.
bidoainfu.com is a top-level domain, while www.biaodianfu.com is not a top-level domain, he is in the domain of biaodianfu.com, called www of the host. After the first-level domain there are second-level domains, third-level domains, as long as I bought a top-level domain, and I built their own BIND server (or other software built) registered to the Internet, then I can feel free to add a few more domains in front (the maximum depth of the tree in the DNS domain name space shall not exceed 127 levels, and each node in the tree can store up to 63 characters). For example, a.www.biaodianfu.com, in this URL, www.biaodianfu.com becomes a second-level domain instead of a host with the host name a.
DNS tree structure diagram.
DNS server types
Roughly speaking, DNS servers have the following types.
- Root DNS servers. There are logically 13 root servers (i.e., 13 IP addresses), distributed around the world. Since the maximum length of UDP query and response messages is 512 bytes, to ensure that the root server data can be included in a single UDP packet, only a maximum of 13 root DNS servers, named from A to M, are allowed to exist.
- Top-level domain DNS servers. These servers are responsible for DNS lookups for top-level domains, such as com, org, net, etc., as well as country top-level domains.
- Authoritative DNS servers. Specific organizations need to maintain corresponding DNS records in order to make their domain names publicly accessible. You can choose your own authoritative DNS server to maintain these records, or you can choose to pay a fee to store them in the authoritative DNS server of a service provider.
- Local DNS servers. For an ISP, there is a local DNS server that takes on the role of a proxy. It is not strictly part of the DNS hierarchy.
DNS communication process
Two types of DNS queries.
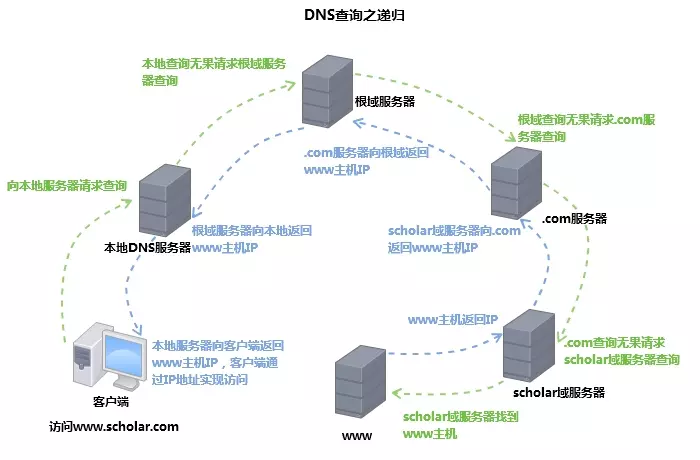
- Recursive query: A recursive query is a DNS server query mode in which a DNS server receives a client request and must reply to the client using an exact query result. If the DNS server does not store query DNS information locally, then that server queries another server and submits the returned query results to the client.
- Iterative Query: Another query mode for DNS servers is iterative query, where the DNS server does not reply directly to the query result when the client sends a query request, but instead tells the client the address of another DNS server, and the client submits the request to this DNS server, and so on until the query result is returned.
Parsing methods.
- Forward parsing: FQDN -> IP
- Reverse resolution: IP -> FQDN
FQDN:(Fully Qualified Domain Name) is a full name domain name. Forward resolution is two different namespaces are two different resolution trees, so each needs a resolution library to be responsible for the forward and reverse of the local domain name respectively.
Recursive: After a DNS request is accepted by a server, if it falls under the jurisdiction of this server it requests a higher-level server to deliver the request in turn and deliver the result in turn to the requesting host.
Iteration: After the DNS request is accepted by the server, if it is not under its own jurisdiction, let the client access the root domain server, and then follow the domain to notify the client to access the lower level server, until finally the client accesses the server that governs the requested domain name.
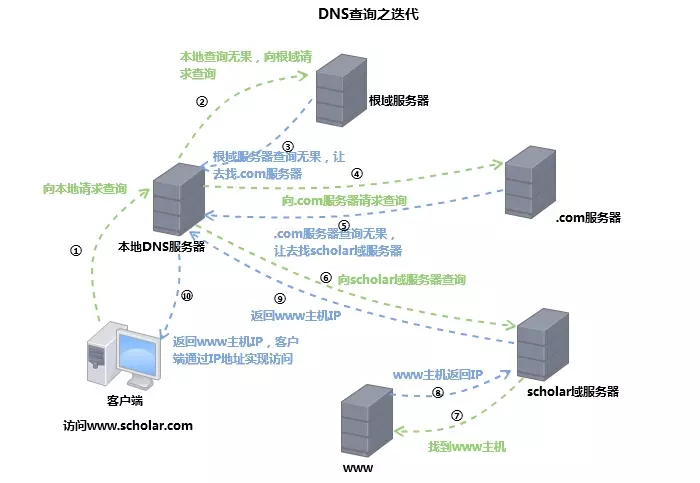
For example, to access an address at www.baidu.com, the DNS query process consists of a recursive query and an iterative query.
- Querying the local browser cache
- Querying the local hosts file
- Requesting the local DNS server for a domain name query (the query up to this point is recursive)
- Requesting the root DNS server if the local DNS server does not have a cache of the corresponding address, returning the address of the com top-level DNS server.
- Request com top-level DNS server to get the address of the com authoritative DNS server
- request the com authoritative DNS server and get the address of www.google.com (queries up to this point are iterative)
The following figure illustrates this query process:
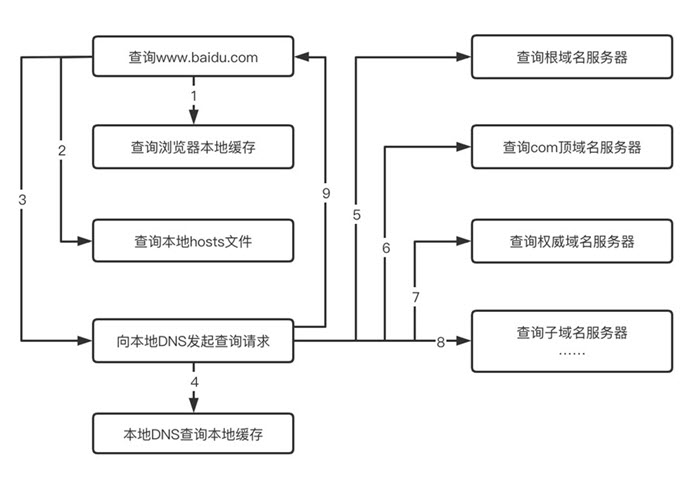
Obviously, if every query went through this entire process, it would be unacceptably time consuming, so DNS caching was created. Across the DNS network, when a DNS server receives a DNS answer, it will cache it locally so that it will respond directly for the same domain name some time in the future (e.g. 2 days), thus reducing the number of requests.
DNS record type
A DNS server actually stores a Resource Record (RR), which consists of the following four fields: Name, Value, Type, and TTL. where TTL indicates when the record should be removed from the cache, and the remaining three fields have the following meanings in different combinations.
Each DNS record has a type. This type defines the meaning of the record’s contents. For example, a DNS record of type MX contains the location of the mail exchange server. All record types are strictly defined in the so-called RFC (Request for Comments). Since the inception of the DNS, many new record types have been added. Some record types have also been declared obsolete because they have been replaced by newer record types.
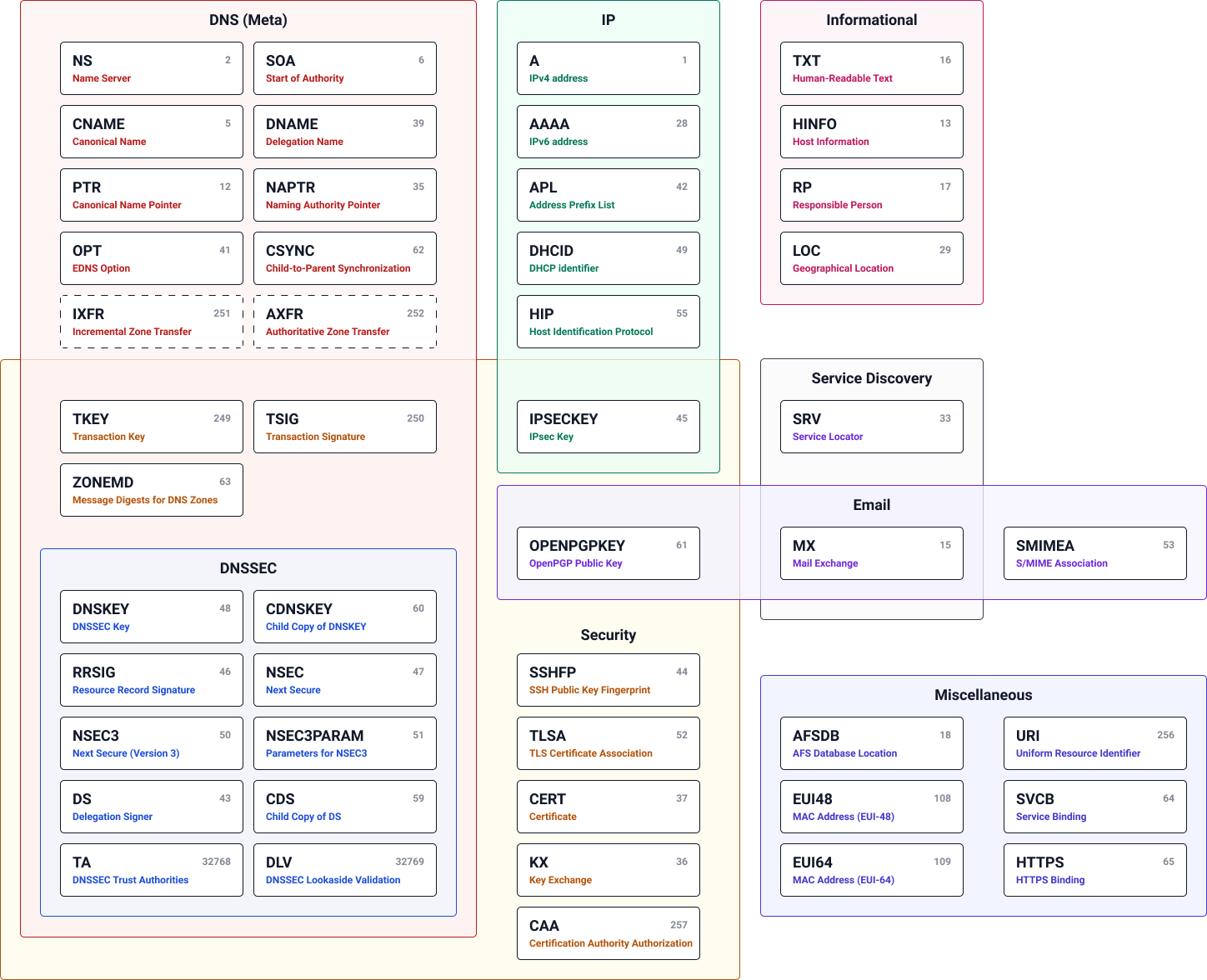
Many different types of DNS records exist. Most of them are used only occasionally. Only a few record types are used very frequently.
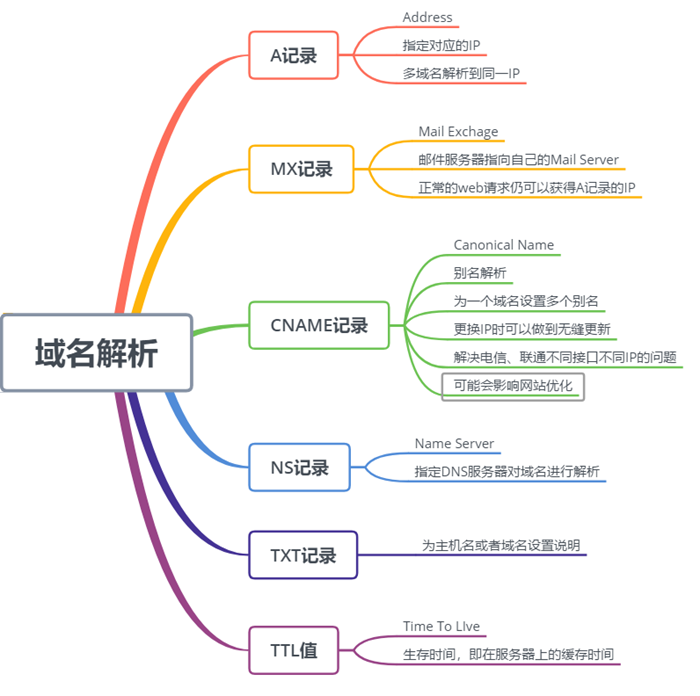
These are the most common types of DNS records.
DNS server construction
BIND installation
BIND (Berkeley Internet Name Domain) service is the most widely used, safe, reliable and efficient domain name resolution service program in the world.
DNS domain name resolution service as the Internet infrastructure services, its responsibility can be imagined, so it is recommended that you install and deploy the bind service program in the production environment with chroot (commonly known as the cage mechanism) extension package, in order to effectively limit the bind service program can only operate on their own configuration files to ensure the security of the entire server.
Installation of the bind service and startup steps.
Main groups of files for DNS configuration.
- /etc/hosts: a list of files for hosts, add records such as:111.13.100.92 www.baidu.com, for simple host name resolution (dotted division representation), by default /etc/named.conf usually tells the program to look at this file first before requesting DNS or NIS network name servers.
- /etc/resolv.conf: conversion program configuration file that must tell the program which name server and IP address to use for this task when configuring the program to request the BIND domain name lookup service for a host name
- /etc/named.conf: the main BIND file that sets the general name parameter and points to the information source of the domain database used by that server
- /var/named/named.ca: root DNS server pointing file, pointing to the root DNS server, used to tell the cache server to initialize
- /var/named/localhost.zone: localhost zone forward domain name resolution file, used to convert the local IP address (0.0.1) to the local loopback IP address (127.0.0.1)
- /var/named/name.local: localhost zone reverse domain name resolution file, used to convert localhost name to local loopback IP address (0.0.1)
- /etc/named.rfc1912.zones: zone settings file
Main configuration information of the name.conf file.
- acl: defines the access control list for ip addresses
- control: defines the control channel used by rndc
- include: Include other files in the configuration file
- key: defines the security key for authorization
- logging: defines the content and location of logs
- options: defines global configuration options and defaults
- server: defines the characteristics of the remote service
- zone: defines a zone
Configuring DNS forward resolution
When configuring the Bind service, the following three main configuration files are used.
- Main configuration file (/etc/named.conf): used to define the operation of the bind service program.
- Zone configuration file (/etc/named.rfc1912.zones): used to store the location of the domain name and IP address correspondence. Similar to the directory of books, it corresponds to the specific location where each domain and the corresponding IP address are located. When it is necessary to view or modify, the relevant files can be found according to this location.
- Data configuration file directory (/var/named): this directory is used to save the data configuration file of the real correspondence between domain name and IP address.
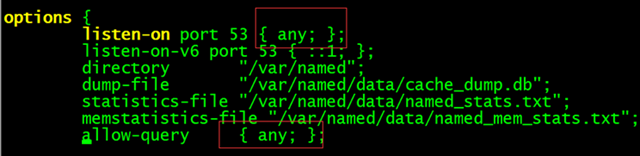
Step 1: Modify the main configuration file /etc/named.conf
Change both the listening address and the address for running queries to any, indicating that all IP addresses on the server are available for DNS resolution services and that everyone is allowed to send DNS query requests to this server, respectively.
Step 2: Modify the zone configuration file (/etc/named.rfc1912.zones)
is used to save the location of the domain name and IP address correspondence. In this file, the location of the file where the domain name and IP address resolution rules are saved and the service type are defined, while no specific information such as domain name and IP address correspondence is included. There are three types of services, hint (root zone), master (master zone), and slave (secondary zone), where master and slave are commonly used to refer to master and slave servers.
DNS default port is 53 TCP and UPD, UDP is for user queries, master and slave replication with TCP and UDP port 53 are used.
BIND’s ACL: bind has four built-in acl:
- none: none of the hosts
- any: any host
- localhost: the local machine
- localnet: the local IP and the network address segment obtained after the mask operation
Note: can only be defined first, then used; so generally defined in the configuration file, in front of the options, but of course can also be customized as follows.
Directives for access control.
- allow-query {}: hosts allowed to query; whitelist
- allow-transfer {}: hosts allowed to zone transfer; (whitelist, generally used for master-slave)
- allow-recursion {}: allow-recursive hosts, recommended for global use
- allow-update {}: allow updates in the zone database
Step 3: Edit the data profile
Copy a copy of the forward resolved template file (named.localhost) from the /var/named directory, then fill in the data configuration file with the corresponding data for the domain name and IP address and save it. Remember to add the -a parameter when copying, this preserves the owner, group, permission attributes, etc. of the original file so that the bind service program can read the file contents smoothly.
|
|
Step 4: Check the configuration, restart the service and test
Check and restart the service.
|
|
Test.
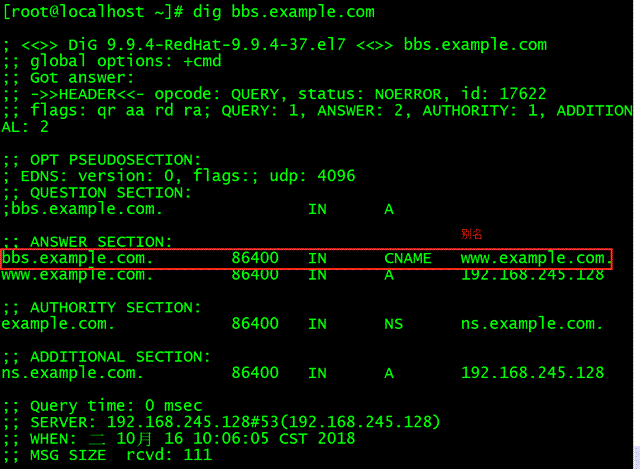
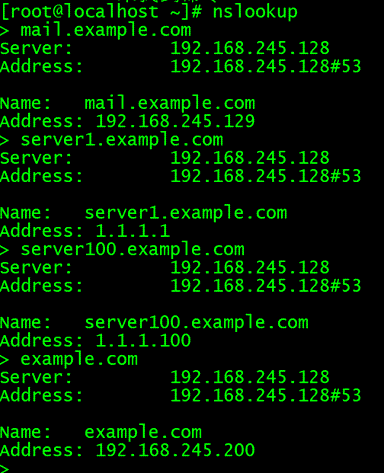
Configuring DNS Reverse Resolution
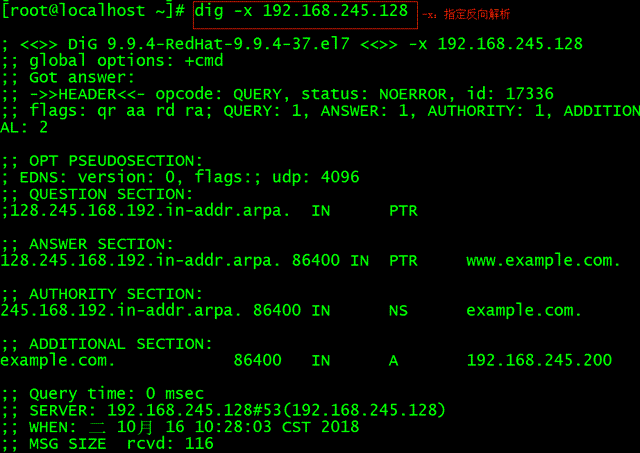
In the DNS domain name resolution service, reverse resolution is used to resolve the IP address submitted by the user to the corresponding domain name information. It is generally used to block all the domain names bound on a certain IP address as a whole and block spam sent by certain domain names. It can also perform reverse resolution for a certain IP address to roughly determine how many websites are running on it. When purchasing web hosting, you can use this feature to verify that the web hosting provider does not have serious overselling issues.
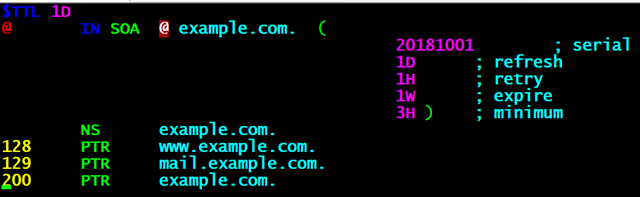
Step 1: Configure the zone file
Reverse resolution is to resolve IP addresses into domain name format, so when defining the zone (zone) should be to reverse the IP address, for example, the original is 192.168.10.0, the reverse should be 10.168.192, and only the network bits of the IP address can be written.
Step 2: Edit data profile
Reverse resolution is to resolve the IP address into a domain name format, so in the definition of zone (zone) should be to reverse the IP address, such as the original is 192.168.10.0, reverse should be 10.168.192, and only the network bits of the IP address can be written.
Step 3: Check the configuration file, restart the service, and test
Build a DNS master-slave server
This serves as a backup resolution record and load balancing, so by deploying a slave server you can reduce the load pressure on the master server and also improve the efficiency of user queries.
Step 1: Allow update requests from the slave server in the zone configuration file of the master server, i.e., modify the allow-update {host address to allow update of zone information;}; parameter, and then restart the DNS service program of the master server.
|
|
Step 2: Fill in the IP address of the master server and the region information to be captured in the slave server, and then restart the service. Note that the service type should be slave and no longer master. masters should be followed by the IP address of the master server, and the file parameter defines the location where the synchronized data configuration file will be saved to, so you can see the synchronized files in the directory later.
|
|
Step 3: Test. You can change the DNS address from the service to yourself for address resolution.
|
|
This scenario proves that the DNS master-slave server is successfully built. In the event of a master DNS failure, the DNS slave server will be automatically utilized for resolution, achieving some degree of fault tolerance.
Configuring DNS security for encrypted transfers
TSIG mainly uses cryptographic encoding to protect the transfer of zone information (Zone Transfer), i.e. TSIG encryption mechanism ensures the security of domain name zone information transfer between DNS servers.
Step 1: Produce keys on the primary service
The dnssec-keygen command is used to generate a secure DNS service key in the format of “dnssec-keygen [parameter]”, with the following common parameters and roles.
| Parameter | Role |
|---|---|
| -a | Specify encryption algorithms, including RSAMD5 (RSA), RSASHA1, DSA, NSEC3RSASHA1, NSEC3DSA, etc. |
| -b | Key length (HMAC-MD5 key length is between 1 and 512 bits) |
| -n | Type of key (HOST indicates host-related) |
Use the following command to generate a 128-bit HMAC-MD5 algorithm key file with the hostname master-slave. The public and private key files are generated by default in the current directory after executing this command, and the secret key is used in the transfer configuration file.
|
|
Step 2: Create the authentication secret key file in the master server
Go to the directory used by the bind service program to save the configuration file, and write the key name, encryption algorithm and private key encryption string just generated to the tansfer.key transfer configuration file according to the following format. For security reasons, we need to change the group the file belongs to to named and set the file permissions to be smaller, and then make a hard link to the /etc directory for the file.
|
|
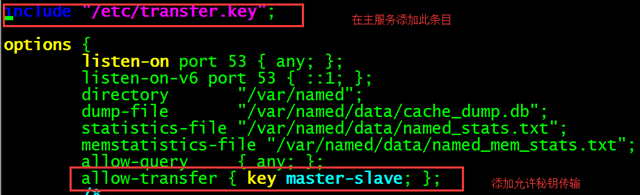
Step 3: Enable the master server key authentication function
Turn on and load the key authentication feature of the Bind service. You first need to load the key authentication file in the master server’s master configuration file, and then set it so that only DNS servers with master-slave key authentication are allowed to synchronize data profiles.
|
|
At this point, the TSIG key encryption transfer function of the DNS master server has been configured. At this point, clear all data configuration files in the DNS slave server synchronization directory, and then restart the bind service program again, at which point the configuration file of the master server will no longer be available.
Step 4: Configure the slave server to support secret key authentication
|
|
Step 5: Configure the slave server configuration file
|
|
After restarting the service, you can see the synchronized files in the /var/named/slaves/ directory.
Configuring a DNS Caching Server
A DNS caching server is a type of DNS server that is not responsible for maintaining domain name data.
Simply put, a caching server saves the resolution records of domain names and IP addresses that are frequently used by users locally on the host computer, thus improving the efficiency of the next resolution. DNS caching servers are generally used in corporate intranets that frequently access certain fixed sites and have high requirements for the access speed of these sites, but they are not widely used in practice. Moreover, whether the cache server can resolve successfully is also related to the permission policy of the designated parent DNS server.
|
|
Free DNS Service Resources
Free Domain Name Resolution Service
General domain name using the registrar to provide domain name resolution services, although convenient, but most of the features are limited, especially at present, China’s domestic will also be blocked for some DNS servers(fuck GFW), resulting in the website can not be resolved, therefore, the use of third-party domain name resolution services is also a necessary choice for Chinese websites, here are some common free domain name resolution services.
Free services provided by domain name registrars
-
Godaddy: You can use Godaddy’s domain name resolution service even if you don’t register your domain name with Godaddy, the way to use it is very simple, after logging into Godaddy website, click “Add Off-site DNS” to add user’s domain name, then set the DNS of user’s domain name to the address specified by Godaddy. After the DNS of the user’s domain name is set to the address specified by Godaddy, you can click on the added domain name for DNS resolution setting after the DNS of the domain name takes effect.
-
NameCheap: The well-known domain name registrar NameCheap also provides free DNS domain name resolution, like Godaddy, after clicking “FreeDNS”, you can add the user’s domain name, and the user can verify their domain name by modifying DNS or domain name email. NameCheap’s resolution services support features such as: URL forwarding (can hide the original URL, support 301 redirects), mail forwarding, A records, CNAME alias records, MX mail records, TXT text records, NS records, AAAA records (IPV6), dynamic domain name resolution and so on.
China’s free domestic domain name resolution service
- DNSPod: DNSPod is a free DNS resolution service that has been in operation for a long time in China and provides a number of paid services in addition to free services. DNSPod has more features and supports dual-line or three-line intelligent DNS resolution for telecom, Netcom, and education networks, which has a faster resolution speed in China, but is often inaccessible for foreign Google crawlers.
Free Domain Name Resolution Service
- ZoneEdit: A well-known and long-established free DNS resolution service for domain names in the United States, established in 1999. Up to 5 domain names can be added to your free account. Resolution types: A record, AAAA record, TXT text record, LOC record, PTR record, CNAME alias record, MX mail record, URL forwarding, mail forwarding, etc. The interface is super simple, fast and stable.
- NET: is an old American IDC, founded in 1994, is stronger in the field of technology, especially IPV6 applications. This free DNS resolution service can add up to 50 domain names, and can set up A records, AAAA records, CNAME alias records, MX mail records, NS records, TXT records, SRV records.
- FreeDNS: A US free domain name DNS resolution service website with a simple interface, easy registration, support for adding domain names with any suffix, and support for Google Apps services. Free DNS resolution service for domain names has three modes: simple mode can directly set IP pointing, forwarding mode can set 301 permanent redirect and 302 temporary redirect, advanced mode can set A record, AAAA record, CNAME record, MX record, PTR record, TXT record.
CDN service comes with domain name resolution
- CloudFlare: Although its main business is CDN (Anycast), it does not affect its reputation as a free DNS in any way, and moreover this free DNS is really globally distributed (12 nodes) and uses CDN technology.
- Baidu Accelerate Le: Accelerate Le is also mainly a CDN business, incidentally providing DNS domain name resolution, providing anti-CC attacks, free DNS resolution, free sub-provincial resolution, anti-hacking, black chain dark chain protection, page tampering protection services.
Free services offered by hosting services
- Linode: is a VPS hosting seller in the United States, the reputation is quite good, and Linode also provides DNS resolution services for users for free, regardless of the fact that you have not purchased Linode’s VPS hosting, you can use Linode DNS for domain name resolution. Given Linode’s high quality hosting, there is reason to believe in the quality level of Linode DNS. Linode provides five NS servers, which are: linode.com~ns5.linode.com, and the server rooms are located in the United States, Europe and other parts of the world, with fast response time.
Public DNS services
When we use telecom or other carriers’ networks, they will automatically assign DNS to you, but since the current domestic carriers are basically unscrupulous, they often perform DNS pollution when resolving domain names, such as pop-ups related to advertisements or, of course, pop-ups of a website navigation page when you enter the wrong URL. To avoid the above mentioned problems, you can prevent being polluted by the operator DNS by modifying your computer’s local DNS servers.
The most widely known public DNS service is Google Public DNS:
- 8.8.8
- 8.4.4
- 3.2.1 (new)
Since Google’s servers are located outside of the country, they are stable and secure, but often suffer from packet loss due to some force majeure. In addition to Google, 114DNS is currently gaining popularity with a total of three modes of DNS resolution.
- Pure, no hijacking, no more pain of being forced to see ads or vulgar websites, and 114.114.114 and 114.114.115.115
- Block phishing virus and Trojan horse sites to enhance the security of online banking, securities, shopping, games, privacy information Service address: 114.114.119 and 114.114.115.119
- Optional blocking of pornographic websites for schools or parents to protect children and teenagers from pornographic content on the Internet Service address: 114.114.110 and 114.114.115.110
In addition, CNNIC (SNDS) as the official management agency also provides DNS services.
-
- 4.8
- 2.4.8
- 2.1.1
- 2.2.2
Ali Public DNS is a DNS recursive resolution system launched by Alibaba Group with the goal of becoming an integral part of the domestic Internet infrastructure and providing “fast”, “stable” and “intelligent” DNS resolution for Internet users. The goal is to become a part of the domestic Internet infrastructure, providing “fast”, “stable” and “intelligent” free DNS recursive resolution services for Internet users. The advantages of Ali’s public DNS services.
- Ali has high-quality server rooms, networks, bandwidth and other Internet infrastructure resources in the country.
- Ali builds and operates the largest CDN network in the country, and has rich experience in Internet traffic scheduling.
- Ali’s W3C is the largest domain name registrar in China, managing several million domain names. It also has rich experience in DNS management.
- Ali has a large number of excellent technical talents, with very strong independent research and development capabilities and operation and maintenance guarantee capabilities.
DNS server IP address.
- Preferred: 5.5.5
- Alternative: 6.6.6
Public DNS+ is a public domain name resolution service launched by DNSPod with the service IP of 119.29.29.29, similar to other public DNS (such as Google’s 8.8.8.8 and 114dns’ 114.114.114.114), which can provide public recursive resolution service for domain names for all users (different from DNSPod’s original domain name authorization resolution service). Public DNS+ is developed with DNSPod’s years of experience in domain name resolution services and relies on Tencent’s strong resource advantages, aiming to provide users with faster, more accurate and stable recursive resolution services, and we will not maliciously hijack any domain names.
DNS server IP address.
- Preferred: 29.29.29
- Alternative: 254.116.116
Reference
https://www.biaodianfu.com/dns-server.htmlhttps://zh.m.wikipedia.org/wiki/%E4%BA%92%E8%81%94%E7%BD%91%E9%A1%B6%E7%BA%A7%E5%9F%9F%E5%88%97%E8%A1%A8https://www.ruanyifeng.com/blog/2018/05/root-domain.htmlhttps://cshihong.github.io/2018/10/15/DNS%E6%9C%8D%E5%8A%A1%E5%99%A8%E6%90%AD%E5%BB%BA%E4%B8%8E%E9%85%8D%E7%BD%AE/