A new cgroups vulnerability, codenamed CVE-2022-0492, which could be abused to evade containers in order to execute arbitrary commands on the container host.
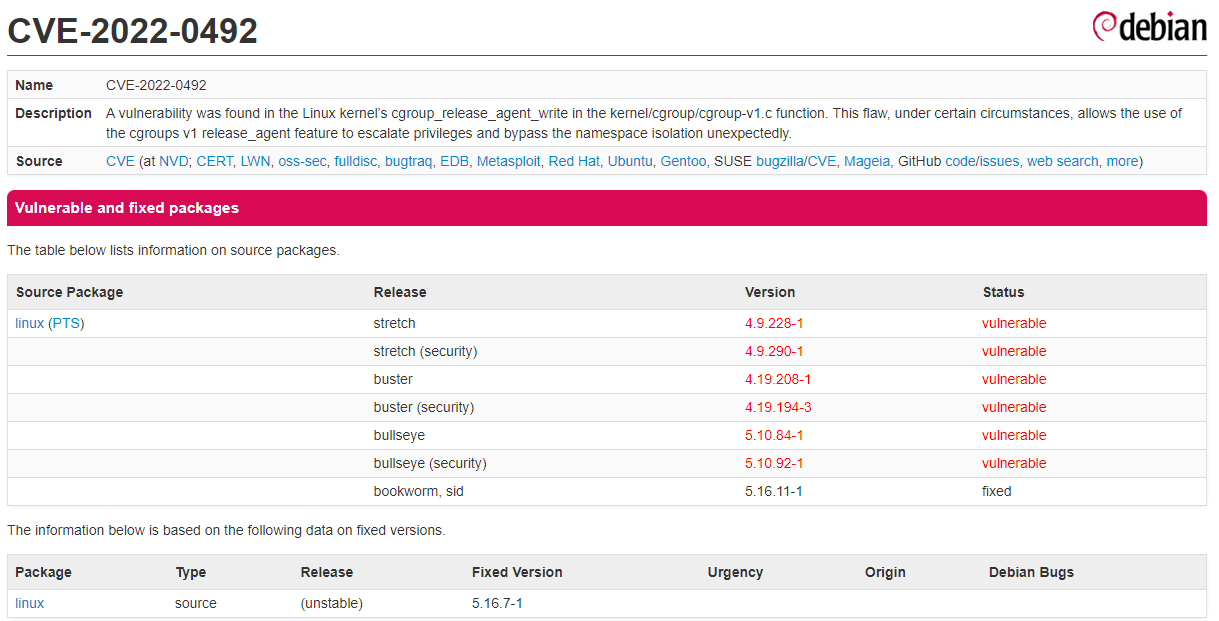
The vulnerability comes from a Linux kernel feature known as cgroups control group, cgroups allows processes to be organized into hierarchical groups so that CPU, memory, and other resource usage, disk I/O, and networking can be limited and monitored.
However, because cgroups lacks internal validation of the release_agent file and fails to properly check whether the process setting the release_agent file has administrative privileges, an attacker can use this cgroups v1 release_agent feature to elevate privileges and accidentally bypass namespace isolation.
That is, if this release_agent file is in the hands of an attacker, the Linux kernel can be forced to invoke it to configure any binary with the highest privileges in release_agent - meaning that the attacker can take over the machine completely.
It is worth noting that only processes with “root” privileges can write to the file, which means that the vulnerability only allows the root process to elevate privileges.