There are only two levels of Linux users: root and non-root, and some users in Linux, such as apache, mysql, nobody, ftp, etc., are also non-root users, i.e. normal users. And these illusions are caused by another concept: user groups
- A user must belong to at least one user group
- A user can belong to more than one user group

The reason for the existence of user groups is still mainly to facilitate the assignment of permissions. While the difference between users themselves and permissions is not very big, the main differences between individual users are.
- whether they have a password or not
- home directory (ordinary users can have a home directory named after their user name, which is stored in /home/username, while the root user’s home directory is: /root)
- shell
Users like nobody, who are used to execute Nginx worker processes, are generally not assigned a password or a shell, and do not even have a home directory. Why don’t you assign a password? If a password is set, the program cannot be used automatically. Since no one will use this user to log in to the system, there is no need to assign a shell. (Note: Actually, technically there is a shell assigned, but the shell assigned is the special shell /sbin/nologin, which does not have any other function, the main function is to prevent you from logging in.)
Linux user and group data
The main repositories of user and group information are the four files in /etc.
- /etc/passwd is a password file that contains basic information about the user.
- /etc/shadow is a shadow password file that contains encrypted passwords.
- /etc/group is a group file that contains basic information about groups and which users belong to them.
- /etc/gshadow is a shadow group file that contains encrypted group passwords.
The password (/etc/passwd) and group (/etc/group) files are shadowed for security reasons. passwd and group files themselves must be readable by all users, but encrypted passwords should not be readable by all users. Therefore, the shadow files contain encrypted passwords, and these files can only be read by root. suid program provides the necessary authentication access, and this program has root privileges but can be run by any user.
All users can be viewed by looking at /etc/passwd. The following is the user information on my system.
|
|
Each line of the file represents a user, and each line is divided by a colon “:” into seven fields, which are structured as follows.
username: password: UID: GID: user full name: home directory: shell
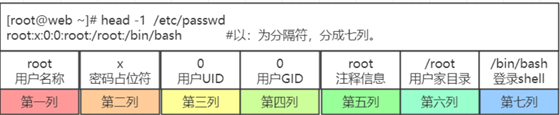
UID.
- UID 0 root user
- UID 1 ~ 999 is accounted for pit users, that is, a write can not log in the user (previously the system is 1 ~ 499, just recently changed)
- UID 1000 above is the normal logable user
GID: previously said a user can belong to more than one user group, but here only one, said the dedicated user group, that is, a user has only one dedicated user group, its affiliation belonging to other user groups is stored in the /etc/group file.
One of the more special is the password field, unified by x instead, see /etc/passwd will know that at the beginning Linux is the password in this file, because of the consideration of /etc/passwd can be viewed by all, so will be stored in the /etc/shadow file (only root privileges can access), the specific data is as follows.
|
|
The structure is as follows.
- login name: encrypted password (means this user cannot be used to login): password last changed date (linux timestamp): minimum number of password days (0 means it can be changed at any time): maximum number of password days: remind the user a few days before expiration: password unavailable period: account expiration date: reserved bit

Again, take a look at the /etc/group file.
|
|
The structure is as follows.
Group name: User group password: GID: User name within the user group
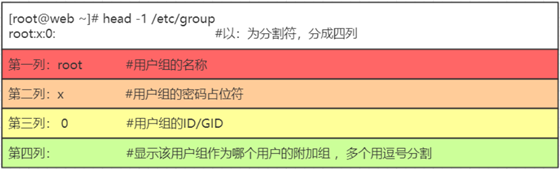
User group passwords are rarely used in normal use and are stored in /etc/gshadow.
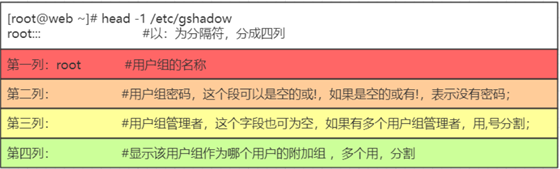
The user group file is special for “user names in user group”, which is actually a list of users under this group, each user is separated by a comma “,”; this field can be empty; if the field is empty, it means that the user group is the user name of GID.
sudo privileges
Ordinary users have very low privileges, even to install software on the system. Many times you can temporarily give privileges to ordinary users, which is sudo (add sudo before the command). For example.
|
|
This is different from Ubuntu and Fedora, which are mainly desktop versions. If you want to give users root privileges, you need to change the /etc/sudoers file and modify its contents.
|
|
To add sudo privileges to no users, simply refer to.
Add the following.
If you want to add sudo privileges to a user group then: (with an extra % unlike for users)
Another way is to add users who do not need to enter the root password, i.e. have root privileges, by adding the following.
|
|
It is also possible to set exactly which execution privileges are available, with the following rules.
authorized users host=[(which users or user groups to switch to)] [whether password authentication is required] command1, [(which users or user groups to switch to)] [whether password authentication is required] [command2], [(which users or user groups to switch to)] [whether password authentication is required] [command3] ……
By default the first time you use sudo, you need to enter the root password, if you execute sudo again within 5 minutes you don’t need to enter the password again, after 5 minutes you need to enter it again. This time is also configurable by adding the following to sudoers.
|
|
where the unit is minutes, and if it is set to 0, it means that the password has to be entered every time.
User and group common operations
Adding users
The useradd command is used to create a new system user in Linux. useradd can be used to create a user account. After the account is created, passwd is used to set the password for the account. The account can be deleted with userdel. The account created with the useradd command is actually saved in the /etc/passwd text file.
Syntax : useradd(option)(parameter)
Options.
-c<comment>: Add the comment text. The comment text will be saved in the comment field of passwd-d<login directory>: Specify the directory where the user will start when logging in.- -D: change the preset value
-e<expiration date>: Specify the expiration date of the account.-f<buffer days>: Specifies how many days after the password expires the account will be closed-g<group>: Specify the group to which the user belongs-G<groups>: Specify additional groups the user belongs to- -m: Automatically create the user’s login directory
- -M: Do not automatically create the user’s login directory
- -n: cancel the creation of groups with the user’s name
- -r: create system account
- -s: specify the shell that the user will use after logging in
- -u: specify the user id
Example.
|
|
Where.
- -s /sbin/nologin set no login
- -d Set user home directory
- -g user group
- -m Create user directory
Modify user password
The passwd command is used to set user authentication information, including user password, password expiration time, etc. It can be used by system administrators to manage the passwords of system users. Only the administrator can specify the user name, general users can only change their own passwords.
Syntax: passwd(option)(parameter)
Options
- -d: removes the password, available only to the system administrator.
- -f: enforce.
- -k: set the password to be updated only after it has expired.
- -l: lock the password.
- -s: lists information about the password, available only to the system administrator; * -u: unlocks the password.
- -u: unlock the locked account.
Ordinary users who want to change their passwords can just run passwd directly. If you create a new user and then want to create a password for the new user, use the passwd username, taking care to create it with the privileges of the root user.
Modify user information
The usermod command is used to modify basic user information. usermod does not allow you to change the name of a user account that is online. When the usermod command is used to change the user id, you must make sure that the user is not running any programs on the computer. You will need to manually change the user’s crontab file. You also need to manually change the user’s at work file. To use NIS server, you need to change the NIS settings on the server.
Syntax: usermod(option)(parameter)
Options
-c<comment>: Modify the comment text of the user account.-d<login directory>: Modifies the directory where the user logs in.-e<expiration date>: modifies the expiration date of the account.-f<buffer days>: modifies how many days after the password expires the account will be closed.-g<groups>: modifies the groups to which the user belongs.-G<groups>; modifies the additional groups to which the user belongs.-l<account name>: modify the name of the user’s account.-L: lock the user’s password to make it invalid.-s<shell>: modify the shell that the user uses when logged in.-u<uid>: modify the user ID.-U:unlock password.
Example, adding newuser2 to the group staff.
|
|
Reference.