Linux is a multi-user, multi-tasking system, often with multiple people working on a single machine at the same time. To protect everyone’s privacy, the role of “file owner” is quite important. When a Linux user logs on to the system, he or she carries a User ID (UID) and a Group ID (GID), which are equivalent to his or her business cards. When you need to access a file or program, you can swipe the card to know if you can read, write, or execute it.
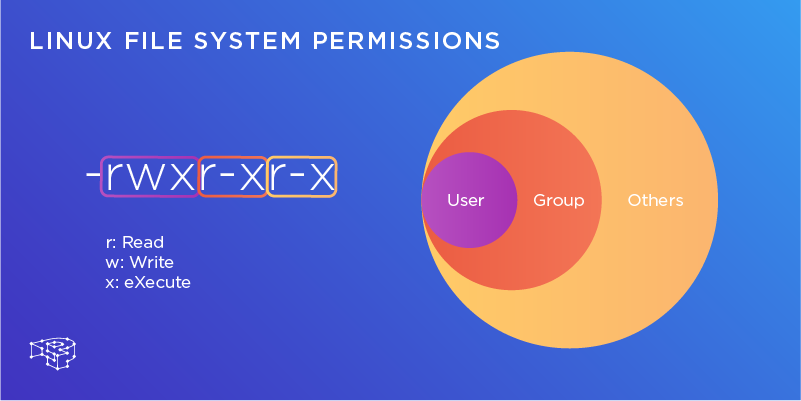
Viewing and interpreting Linux file permissions
Type ls -l in the root directory to see the following information.
|
|
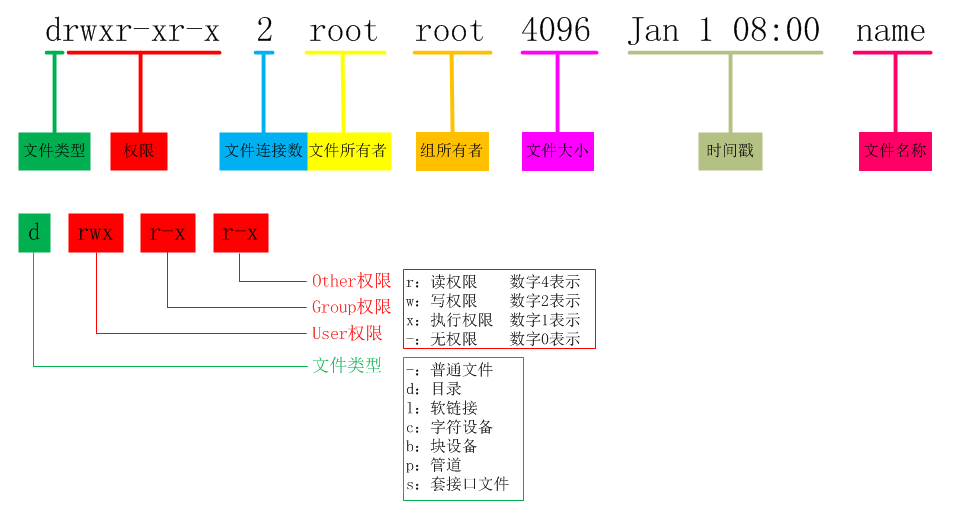
Each record consists of 7 parts, in the order of lrwxrwxrwx. 1 root root 7 Aug 18 21:27 bin -> usr/bin, for example, and the specific representations are
- lrwxrwxrwx. represents the file type and permissions
- 1 for the number of file connections
- root is the owner
- root is the user group it belongs to
- 7 is the file size (in K)
- Aug 18 21:27 represents the last modified time of the file
- bin -> usr/bin filename
Let’s first split the lrwxrwxrwx. string, where the first character is used to describe the type of file, with the following optional values
-represents a normal file- d for directory
- l means this is a soft or hard connection
- b is a block device, such as a disk that holds large blocks of data
- c is a character device, such as a mouse, keyboard, and other devices that require continuous serial reading and writing
- s stands for socket file
- p stands for named pipe file
This file, l, represents a soft connection or hard connection. The nine immediately following characters, which need to be looked at three by three, represent.
- Permissions of the owner
- Permissions of the group it belongs to
- Permissions of other users
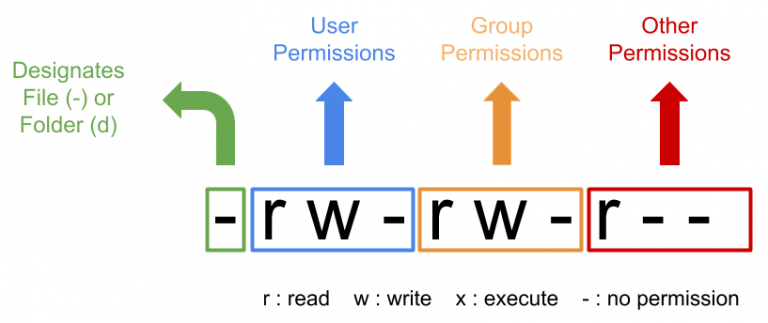
The order is rwx, corresponding to the permissions R ead (read), W rite (write), e Xe cute (execute), or - if you do not have a particular permission.
The last one. It may be confusing to know what it is used for, after checking, the information shows that this point indicates the presence of “SELinux security tag”! If selinux is turned off, this point will not appear.
rwx permissions explained
Also notice that the last file name of this last demo has a -> for soft link or hard link, so let’s learn the difference between soft link and hard link.
- A soft link (also called a symbolic link - symbolic link , symlink or soft link ) is a special type of file that contains a reference to another file or directory in the form of an absolute or relative path. It is somewhat similar to a windows shortcut. It is created by: ln -s source dist
- A hard link is a link through an index node. In the Linux file system, files stored in a disk partition are assigned a number, called the Inode Index, regardless of their type. In Linux, multiple file names pointing to the same index node exist. Generally this connection is a hard join. The purpose of a hard link is to allow a file to have multiple valid pathnames so that the user can create hard links to important files to prevent “accidental deletion”. The reason for this is as described above, because the index node corresponding to that directory has more than one connection. Deleting only one connection does not affect the index node itself and the other connections, but only when the last connection is deleted, the file’s data block and the directory’s connections are released. In other words, a file is only truly deleted if all hardwired files associated with it are deleted. The creation method is: ln source dist
With some combing, some similarities and differences between soft and hard connections can be seen.
- There is little difference in use, both are equivalent to a file with a different path or filename
- If you enter the target file to delete the file link, the soft link will fail, the hard link will only be “link number-1”
- Soft links can be created in any location, including the network, while hard links must be on the same disk
More details about soft and hard links will be presented when we organize inode related knowledge.
Linux file permissions modification
The next thing you learn is to modify the attributes and permissions of a file, and the first thing you learn is to modify the user or user group to which it belongs. Command format: chown [-R] username:group filename (where -R is used when modifying folders and represents a recursive modification.)
There are two methods to modify read and write permissions.
numeric method
The permission rwx corresponds to 4,2,1, which is actually a 3-digit binary, if only read permission is 4, if the user has read and write permission, then it is 4+2=6, and so on.
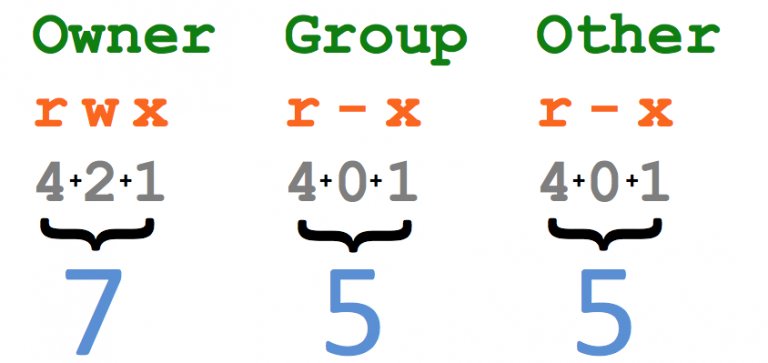
chmod 700 filename is executed by setting the user to have read and write access, while the user group and other users have no access.
| # | permissions | rwx | binary |
|---|---|---|---|
| 7 | Read + Write + Execute | rwx | 111 |
| 6 | read + write | rw- | 110 |
| 5 | Read + Execute | r-x | 101 |
| 4 | Read Only | r- | 100 |
| 3 | write + execute | -wx | 011 |
| 2 | write-only | -w- | 010 |
| 1 | execute only | -x | 001 |
| 0 | none | - | 000 |
Text method
The text method starts with introducing four letters: u, g, o, and a, where u stands for u ser, g stands for g roup, o stands for o ther, and a stands for all. in addition, you need to learn three symbols: +, -, and =, which stand for adding, subtracting, and setting, respectively. e.g., chmod ug+w filename, which means adding write permissions to filename, which means adding write permission to the user and user group of filename.
Additional content
Masking files
The initial ls -l doesn’t actually show all the files in the directory, you can use ls -al to show all the information:.
|
|
You can see that root’s home directory has many files preceded by . These files are hidden files in Linux, in Linux will be files in front of the file name plus a . You can hide the file.
Special directories
There are several special directories under Linux: “.” , “…” , “-”, “~”
- “.” Current directory
- “…” Previous directory
- “-” The previous working directory
- “~” The current user’s home directory
Special File Permissions
Linux files have two special permissions, s and t, in addition to rwx. They are not used much in normal times and are not studied in depth.
chmod: change file permissions
|
|
chown: change file owner
|
|
chgrp: change the group where the file is located
|
|