Here’s the thing. Recently, the group created a new code repository to develop a new product, and since it’s raining hard in Beijing today, many of my colleagues chose to work from home (including me), so I chose to use my own PC to work.
But I used my own personal email address for the Git information on my PC.
If you’ve ever used Git, you’ve probably hit these two lines before, right?
This works globally, so if I use Git’s commit command to commit my code, the commit name and email will be the personal information that I just configured.
And then if I push the code to my company’s repository, it’s going to have a weird username and avatar that looks like this
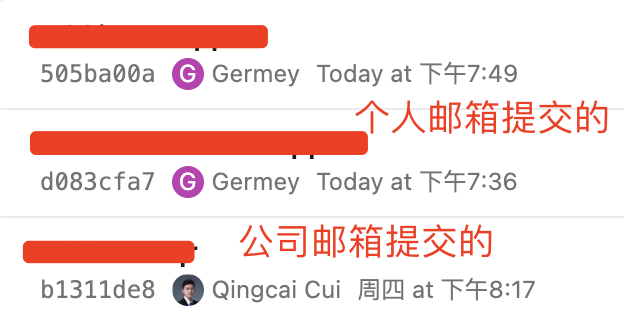
The top two commits in the picture were made from my personal computer, and the last commit was made from my company computer at work last week.
Isn’t this strange?
If other people also use their personal email to commit, there will be all sorts of weird commits in the company codebase and no way to know.
This is definitely not tolerable, if anyone writes strange code in the future, it is not easy to check who wrote it.
So, I had a thought: Why not make a restriction when submitting code?
Can you do it? Of course you can!
Translated with www.DeepL.com/Translator (free version)
Realization
There are a number of tools for configuring Git Hook. Git has native support for it, but we can also use third-party libraries to do it.
Currently our code repository is based on Node.js, so a popular solution for configuring Git Hook for Node.js projects is husky, so I’m going to use husky to do it here as well.
First, install husky.
|
|
Then configure a Node.js prepare command, which can be executed automatically after the package Node.js package is installed, so the prepare command is configured as husky initialization script, package.json add the following configuration inside.
OK, so if someone else clones this repository, they will automatically initialize husky after loading all the Node.js packages, and then generate a .husky initialization directory locally in the project, so that Git Hook will take effect.
For example, if you add a pre-commit script to the .husky directory, that script will be pre-executed to do some checking before committing.
So I created a pre-commit script in the .husky directory, and wrote the following.
|
|
This is a Linux shell script, which follows the shell syntax exactly.
Here you actually get the result of git config user.email and then use a regular expression to match whether it matches the company mailbox format.
For example, our company email suffix is of course the microsoft.com suffix, so here we use ^[. [:alnum:]]+@microsoft\.com$ to match. It’s worth noting here why we don’t use \S for non-blank characters, but a [:alnum]? This is because the Bash Shell itself does not support \S matches, so it has to be replaced with [:alnum].
And what if it doesn’t match?
Well, you can just output some error messages, like this one, and use git config --local to configure your username and email. The reason you use -local is because you don’t want it to affect the global Git configuration, so it only works for that repository.
With this configuration in place, let’s try it out.
This time I haven’t made any changes, Git is still configured as it was, i.e. my global personal mailbox configuration.
When I run the commit command, I get an error.
It’s great! It was detected.
Following what this prompt says, I then run the following configuration command.
Here, I configured my company personal information and company email.
Then I run the commit command again, and the error message as above does not appear anymore!
Great job!
With this, we can successfully stop some weird commits from entering our company’s code repository!
Then I sent this PR out, and a colleague seemed to be impressed and said.
Hahaha, with this, we should never see our code repository inside the QQ mailbox again!
I hope it will help you ~
Reference https://cuiqingcai.com/30028.html